Turkey-Aligned Hackers Exploit Zero-Day Vulnerability to Target Iraqi Kurdish Entities
A cyber threat actor, believed to have connections with Turkish governmental interests, has been detected exploiting unpatched user accounts affected by a vulnerability (CVE-2025-27920) in Output Messenger, a multiplatform chat application. This campaign, uncovered by Microsoft Threat Intelligence, has been active since at least April 2024.
Tracked under the name Marbled Dust, this group is recognized as a cyber-espionage entity aligned with Turkish interests. On May 12, Microsoft Threat Intelligence reported with high confidence that the victims of this operation are associated with the Kurdish military in Iraq.
From Exploited Zero-Day to Patched Vulnerability
CVE-2025-27920 is a directory traversal vulnerability due to improper file path handling within Output Messenger version 2.0.62, affecting all prior versions. Attackers can exploit this vulnerability using ‘../’ sequences to access sensitive files outside of designated directories, which may result in configuration leaks or unauthorized file access.
The vulnerability was identified by Microsoft and subsequently addressed in Output Messenger version 2.0.63, as per an advisory issued in December 2024 by Srimax, the Indian-based company developing the application. However, the CVE entry was reported by MITRE on May 5, 2025, with incomplete information regarding the vulnerability’s status and the absence of enriched data, including its severity score (CVSS).
Microsoft also noted the identification of a second vulnerability in Output Messenger (CVE-2025-27921), for which a patch has also been released by Srimax. However, exploitation of this second vulnerability remains unobserved.
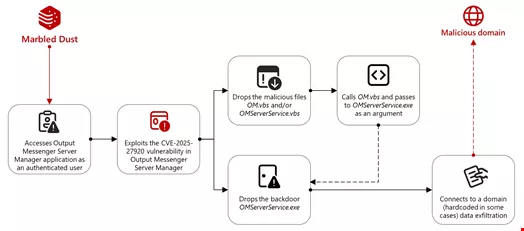
Marbled Dust’s Attack Chain
In the execution of this malicious campaign, Marbled Dust initially gains access to the Output Messenger Server Manager application as an authenticated user, possibly via DNS hijacking or typo-squatted domains that enable the actor to capture and reuse credentials. The compromised account is then leveraged to extract the user’s Output Messenger credentials, followed by exploitation of the CVE-2025-27920 vulnerability.
Reportedly, Marbled Dust began exploiting this vulnerability as early as April 2024, well before it was disclosed and resolved in an Output Messenger patch. The group has continued to exploit unpatched systems even after the release of the fix by Srimax.
Using the CVE-2025-27920 exploit, Marbled Dust installs a series of malicious files (OM.vbs, OMServerService.vbs, and OMServerService.exe) into specific directories of the Output Messenger server. The malware, OMServerService.vbs, initiates a connection to the Golang-based backdoor, OMServerService.exe. This executable then connects to a hardcoded domain (api.wordinfos[.]com), facilitating data exfiltration.
On client machines, the malware retrieves and executes OutputMessenger.exe and OMClientService.exe, another Golang backdoor. OMClientService.exe checks connectivity to the command-and-control (C2) domain, sends hostname data, and executes responses from the C2 using “cmd /c”. The malware has shown observable connections to an IP address attributed to Marbled Dust, presumably for data theft, utilizing plink (the PuTTY SSH client) to gather files and compile a RAR archive on the desktop.
Marbled Dust’s Previous Activity
This campaign has successfully gathered user data from Iraqi targets, reflecting the previously noted targeting patterns of Marbled Dust. Since at least 2019, the group has aimed at entities in Europe and the Middle East, particularly focusing on governmental organizations and firms within the telecommunications and IT sectors.
Marbled Dust’s behavior has shown parallels with other threat actors such as Sea Turtle, COSMIC WOLF, SILICON, Teal Kurma, and UNC1326. Prior activities included scanning infrastructure for known vulnerabilities in externally facing devices or applications, exploiting these vulnerabilities for initial access.
Additionally, Marbled Dust has been noted for compromising DNS registries or registrars to alter the DNS settings of governmental organizations, allowing traffic interception and credential theft.
Microsoft researchers highlighted, “This new attack indicates an evolution in Marbled Dust’s capabilities while retaining a consistent operational method.” The effective use of a zero-day exploit signifies a potential increase in their technical sophistication and a possible escalation in their targeting motivations or operational urgency.








