Malware Discovered on Google Play and Apple App Store: Compromising Personal Photos and Cryptocurrency Assets

A recently identified mobile malware, known as SparkKitty, has been found on both Google Play and Apple App Store, specifically targeting Android and iOS devices. This advanced malware is suspected to be an evolution of a previously recognized strain, SparkCat, which was detected by Kaspersky in January. SparkCat was notable for employing optical character recognition (OCR) techniques to extract cryptocurrency wallet recovery phrases from images on compromised devices.
The installation of crypto wallets often prompts users to note down their wallet’s recovery phrase, which should be stored securely offline. This seed phrase is critical as it can be used to recover a crypto wallet and its associated assets on different devices, rendering it a prime target for cybercriminals. While some users may opt to take screenshots of their seed phrases for convenience, this practice significantly compromises security.
According to a report from Kaspersky, SparkKitty malware indiscriminately gathers all images from the photo gallery of infected devices. While the primary goal appears to be the extraction of crypto wallet seed phrases, the acquired images could also be exploited for a range of malicious activities, including extortion, if they contain sensitive content.
SparkKitty Malware Overview
The SparkKitty campaign has reportedly been operational since at least February 2024, proliferating through both official app stores and unofficial distribution platforms. Kaspersky identified two primary malicious applications: 币coin on the Apple App Store and SOEX on Google Play, both of which had been removed at the time of writing.
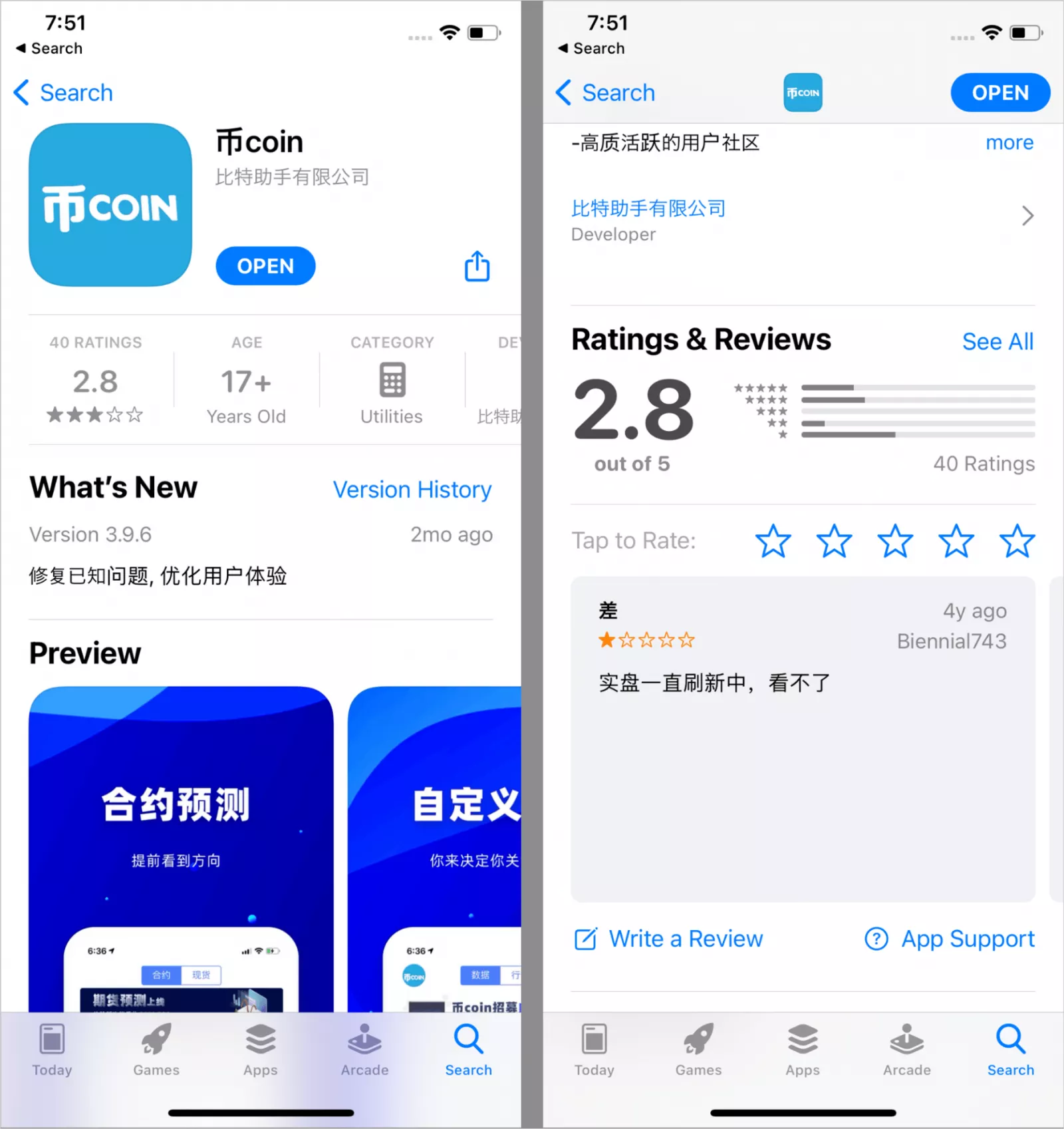
Source: Kaspersky
SOEX is categorized as a messaging application with inherent cryptocurrency exchange functionalities and had over 10,000 downloads from the official Android app store.
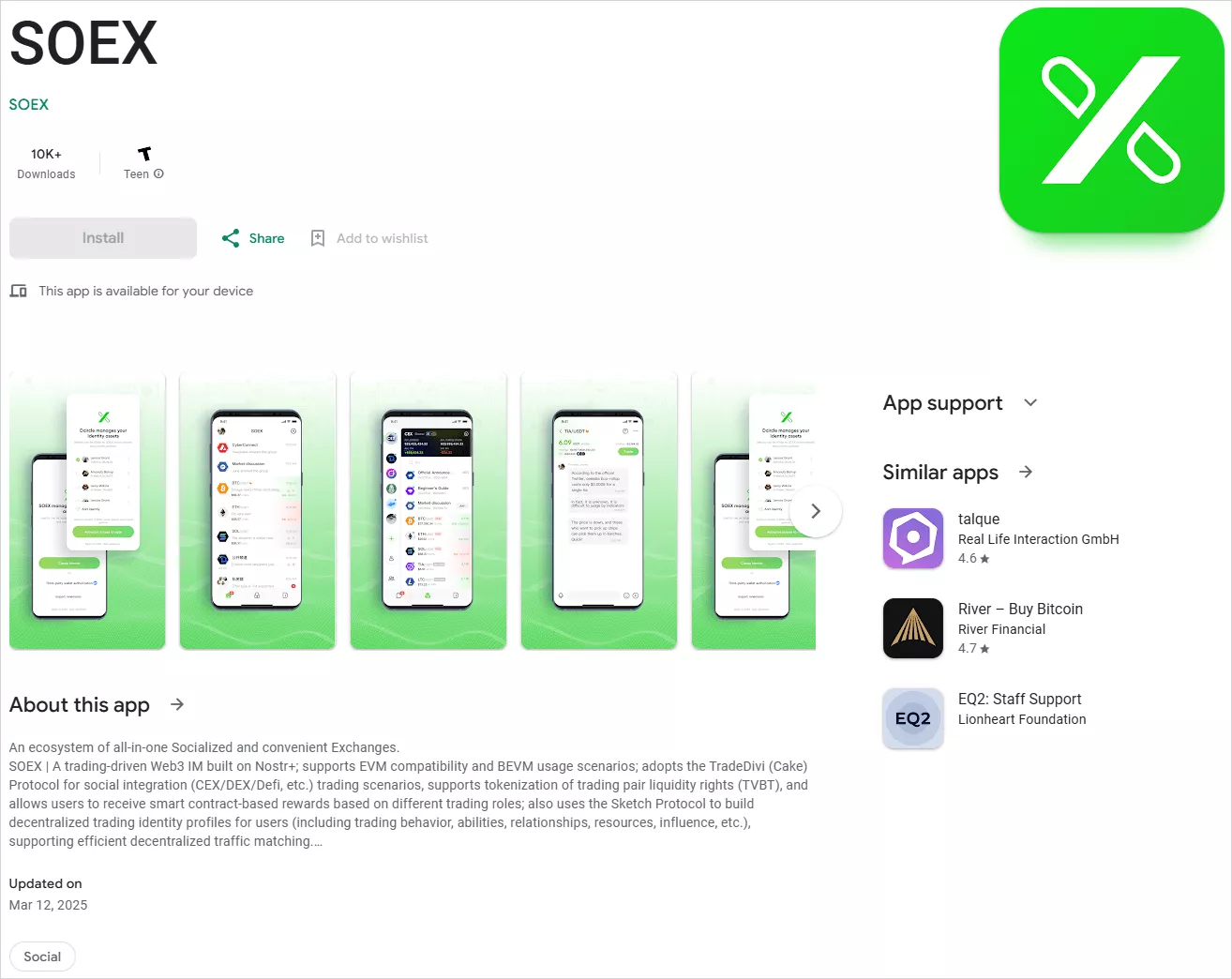
Source: Kaspersky
Kaspersky also reported that modified TikTok clones embedding deceitful online cryptocurrency stores, gambling applications, and adult-themed games comprised additional vectors for distributing SparkKitty, particularly via unofficial channels.
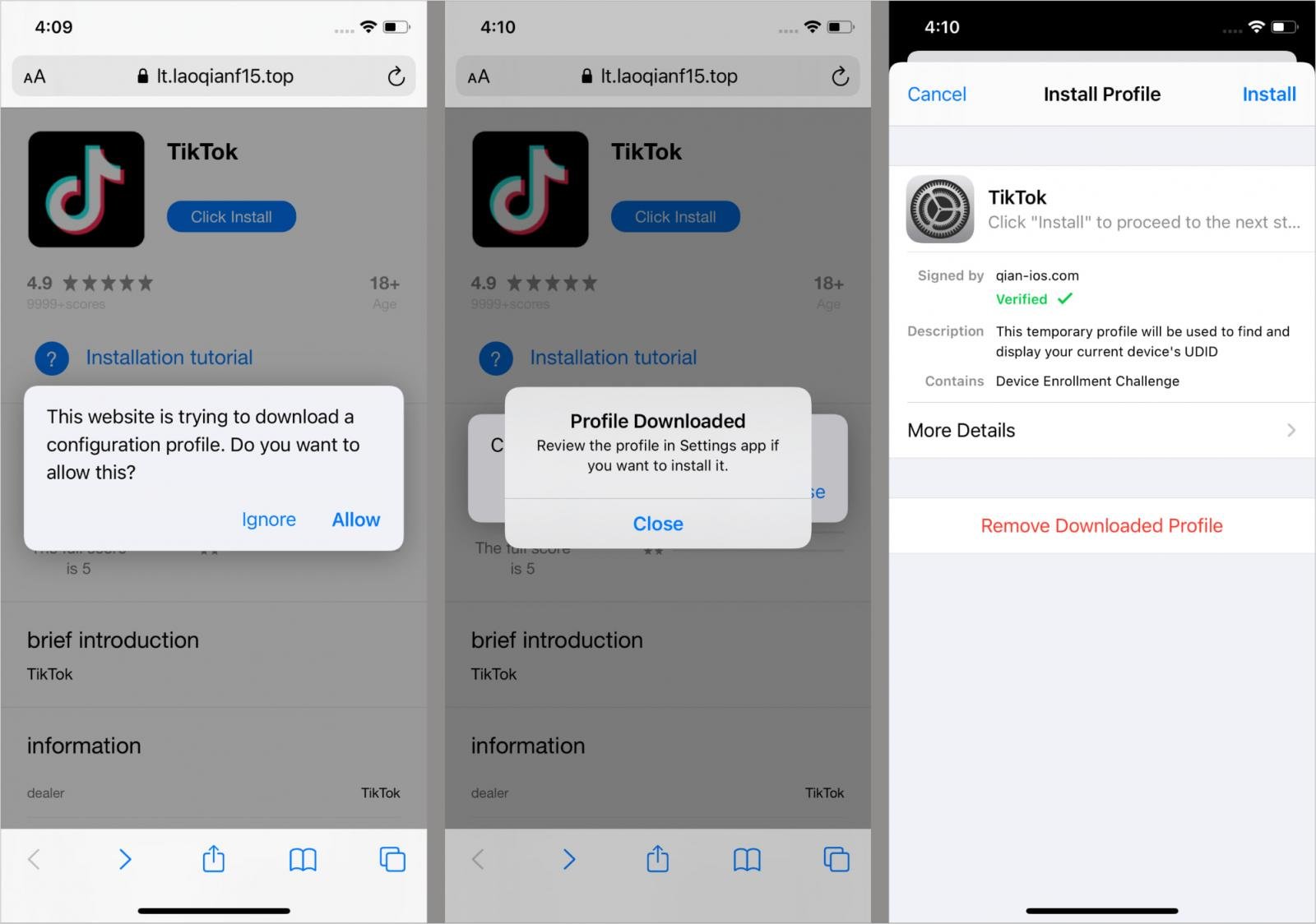
Source: Kaspersky
On the iOS platform, SparkKitty is camouflaged as fake frameworks, such as AFNetworking.framework and libswiftDarwin.dylib, and is sometimes disseminated through enterprise provisioning profiles. In contrast, the Android variant is embedded within Java/Kotlin applications, with some versions utilizing malicious Xposed/LSPosed modules.
The malicious framework initiates automatic code execution on the app launch in iOS by employing the Objective-C ‘+load’ method, following a configuration verification through the app’s Info.plist. Execution continues only if the values correspond to predetermined strings. On Android, the malware activates during the app launch or upon specific user actions, such as navigating to designated screens. Upon activation, it retrieves and decrypts a remote configuration file using AES-256 (ECB mode) to acquire command-and-control (C2) URLs.
On iOS, the malware requests access to the photo gallery, whereas on Android, it solicits users to grant storage permissions for accessing images. If permissions are granted on iOS, the malware continuously monitors the gallery for modifications and transmits any newly identified or previously unuploaded images.
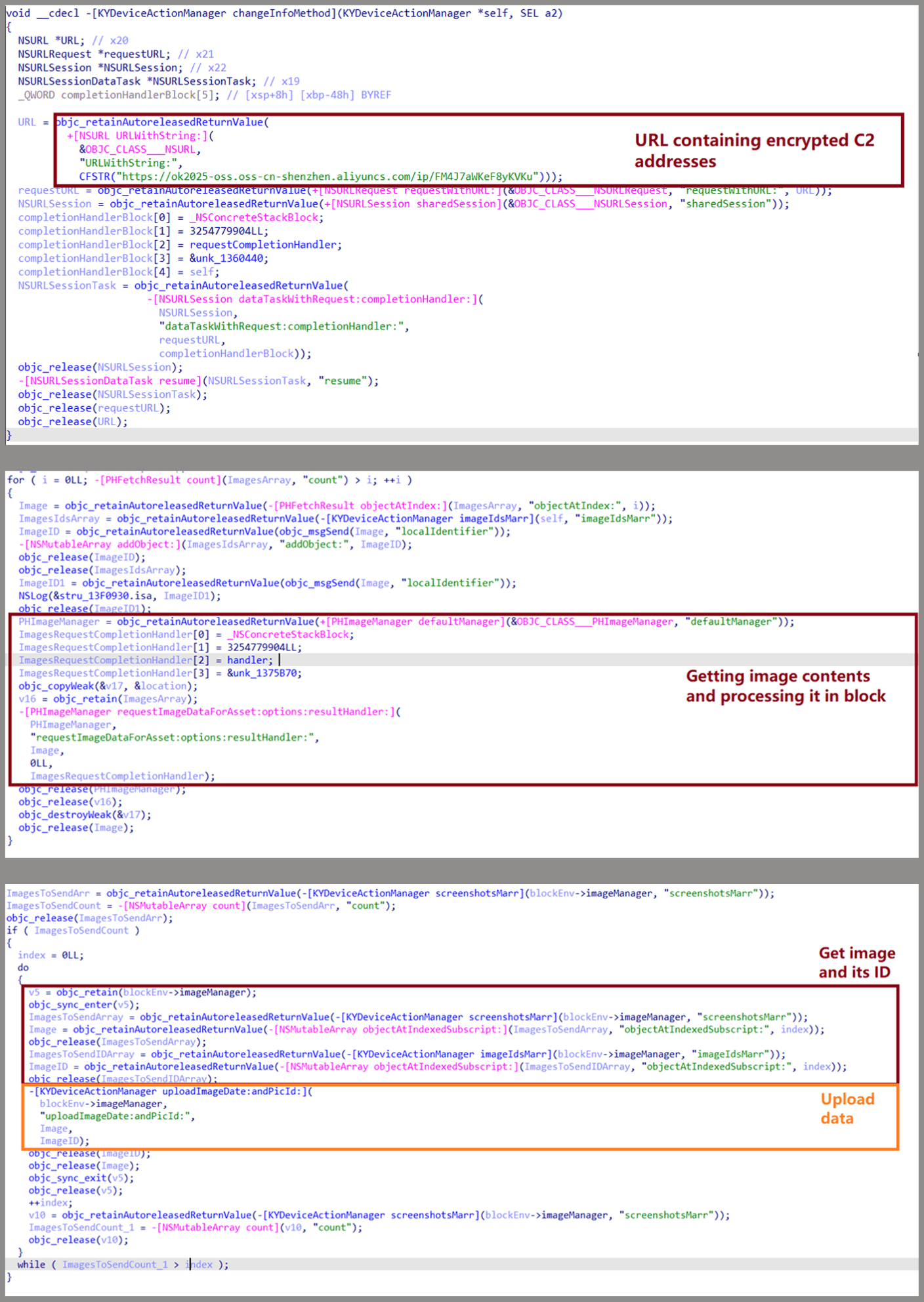
Source: Kaspersky
In the case of Android, the malware uploads images from the gallery along with device identifiers and metadata. Some iterations of SparkKitty utilize Google ML Kit OCR to identify and selectively upload images containing text.
Source: Kaspersky
The emergence of SparkKitty underscores the risk of malware infiltrating official app stores, reinforcing the imperative for users to exercise caution and not rely solely on the legitimacy of software from vetted distribution channels. All applications should be meticulously examined for indicators of fraudulent activity, including suspicious reviews, questionable publisher backgrounds, and an incongruity between download counts and the volume of positive reviews.
Requests for gallery access during installation should be critically evaluated and denied when they do not align with the primary function of the application. On iOS, users should refrain from installing configuration profiles or certificates unless sourced from a reputable origin. Similarly, Android users are advised to enable Google Play Protect within settings and conduct routine full-device scans.
In conclusion, cryptocurrency holders must avoid storing images of their wallet seed phrases on mobile devices due to the active targeting of such information by malware. Instead, these sensitive details should be securely stored offline in a designated location.
Responses from Apple and Google have been sought regarding how these malicious applications were permitted to infiltrate their respective app stores. Google stated, “The reported app has been removed from Google Play and the developer has been banned.” They emphasized that Android users are safeguarded against this app by Google Play Protect, which is enabled by default on devices utilizing Google Play Services.
Inquiry has also been made to Apple regarding the identified applications, and updates will be provided as responses are received.








