Hackers Exploit Open-Source Tools to Target Financial Institutions in Africa
Unit 42, the research team at Palo Alto Networks, has uncovered a malicious campaign targeting financial organizations throughout Africa. This campaign, conducted by a group identified as CL-CRI-1014, has been active since at least 2023. The attackers are believed to operate as initial access brokers (IABs), gaining entry to victim networks and subsequently selling access to other malicious actors on the dark web.
The attackers employ a variety of open-source tools to facilitate their operations, including PoshC2—an attack framework—as well as Chisel, a tunneling utility. They also utilize readily available software such as Microsoft PsExec and Classroom Spy, a remote administration tool that has replaced the previously employed MeshAgent in earlier campaigns.
The threat actors establish tunnels for network communications and engage in remote administration activities to maintain control over compromised systems.
Attack Chain Explained
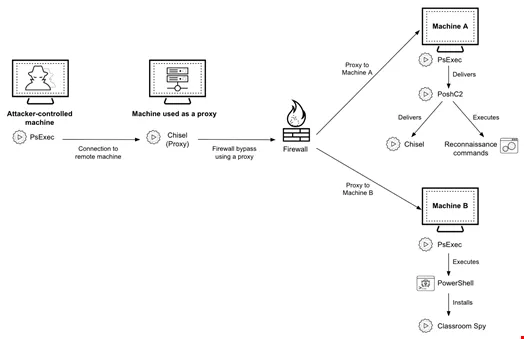
The attack chain associated with the recent CL-CRI-1014 campaign can be summarized as follows:
- The threat actor utilizes PsExec to connect remotely to a secondary machine, which acts as a proxy.
- Chisel is utilized on the proxy machine to circumvent firewall protections within the target organization’s system, allowing connections to multiple machines.
- PsExec is deployed on some machines to deliver PoshC2 and perform reconnaissance, with network traffic tunneled via Chisel.
- On other machines, PsExec runs PowerShell to install Classroom Spy.
PoshC2 serves as a pivotal tool for the attackers, allowing them to execute commands and establish footholds in compromised environments. The framework is versatile, supporting the generation of various implant types including PowerShell, C#.NET, and Python, and comes preloaded with multiple attack modules.
Classroom Spy features include:
- Live monitoring of computer screens (capable of capturing screenshots)
- Mouse and keyboard control
- File collection and deployment to/from machines
- Webpage visitation logging
- Keylogging capabilities
- Audio recording
- Camera access
- Terminal access
- System information collection
- Application monitoring and blocking
To evade detection, CL-CRI-1014 employs various tactics, such as utilizing packers, signing its tools with stolen certificates, and incorporating icons from legitimate software products.
There is currently no evidence suggesting that the campaign exploited vulnerabilities in the target organizations’ products or services.








