Google Addresses Critical Chrome Vulnerability with Active Public Exploit Mitigation

Google has issued critical security updates to address a high-severity vulnerability in the Chrome web browser that could enable attackers to gain unauthorized access to user accounts upon successful exploitation.
While there is no confirmation of this vulnerability being actively exploited, Google has acknowledged the existence of a public exploit, which often indicates potential real-world application of the flaw.
“Google is aware of reports that an exploit for CVE-2025-4664 exists in the wild,” Google stated in a security advisory released on Wednesday.
The vulnerability, identified by Solidlab security researcher Vsevolod Kokorin, is characterized as an insufficient policy enforcement issue in Chrome’s Loader component. This flaw permits remote attackers to extract cross-origin data through malicious HTML pages.
Kokorin explained, “Unlike other browsers, Chrome resolves the Link header on subresource requests. The problem arises from the Link header’s ability to set a referrer-policy, which can include unsafe-url, capturing full query parameters.”
“These query parameters may contain sensitive information— for instance, during OAuth flows, this can facilitate an account takeover. Developers often overlook the potential for extracting query parameters through an image from a third-party resource.”
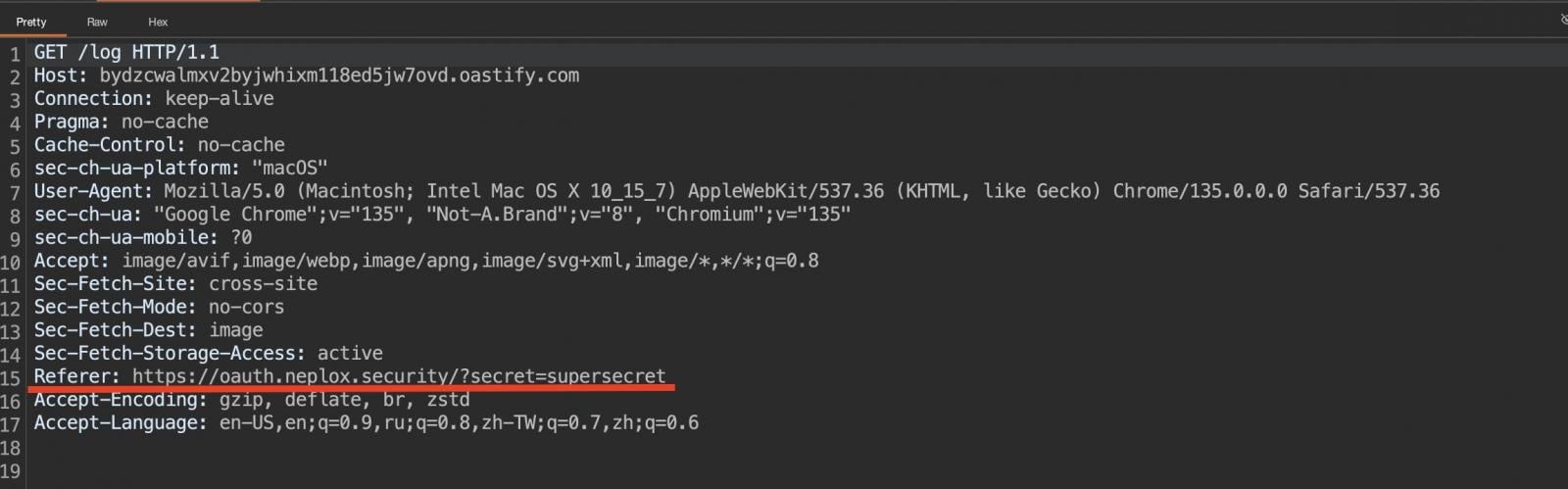
Google has implemented the necessary fixes for users operating on the Stable Desktop channel, with the patched versions (136.0.7103.113 for Windows/Linux and 136.0.7103.114 for macOS) rolled out globally.
Although Google indicates that the security updates will be distributed over the coming days and weeks, they were found to be immediately available upon check for updates.
Users opting to avoid manual updates can configure Chrome to check for and install updates automatically upon subsequent launches.
Earlier in March, Google addressed another high-severity zero-day vulnerability (CVE-2025-2783) that was exploited in targeted espionage operations against Russian government bodies, media entities, and educational institutions.
Researchers at Kaspersky uncovered this zero-day vulnerability, revealing that attackers used exploits of CVE-2025-2783 to circumvent Chrome’s sandbox protections, allowing them to infect targets with malware.
In the previous year, Google patched a total of 10 zero-day vulnerabilities, many of which were disclosed during the Pwn2Own hacking competition or exploited in various attacks.








