Enhancing CI/CD Workflow Security with Wazuh
Continuous Integration and Continuous Delivery/Deployment (CI/CD) encompasses practices that automate the development and release of code across various environments. CI/CD pipelines are essential in contemporary software development, ensuring that code undergoes consistent testing, building, and deployment in a rapid and efficient manner.
However, while CI/CD automation enhances the speed of software delivery, it also opens the door to security vulnerabilities. Without implementing appropriate security measures, CI/CD workflows may be susceptible to supply chain attacks, insecure dependencies, and insider threats. To address these vulnerabilities, organizations must incorporate continuous monitoring and enforce security best practices at every stage of the pipeline. Securing CI/CD workflows is critical to maintaining the confidentiality, integrity, and availability of the software delivery process.
Security Challenges and Risks in CI/CD Workflows
Despite the advantages that CI/CD workflows offer in terms of automation and efficiency, they also present distinct security challenges that must be effectively managed to safeguard the development process. Key challenges include:
1. Lack of Visibility and Inadequate Security Monitoring: CI/CD workflows typically involve a diverse array of tools and stages, complicating efforts to maintain security visibility and identify potential threats. Vulnerabilities, particularly in third-party libraries or containerized applications, can pose significant risks that evade detection without proper management. The absence of centralized monitoring hampers real-time threat detection and response, resulting in a heightened likelihood of exploitation due to reactive incident response measures.
2. Compliance Requirements: Balancing the need to meet regulatory standards, such as GDPR or HIPAA, with the demand for rapid deployment cycles presents a significant challenge. Organizations must navigate the complexities of enforcing security policies and ensuring data protection while maintaining efficient CI/CD workflows.
3. Code and Dependency Vulnerabilities: Unpatched or outdated dependencies within the CI/CD pipeline can introduce considerable security risks. Neglected third-party libraries or outdated packages can become vectors for attacks if not regularly updated and monitored for vulnerabilities. The accelerated pace of CI/CD intensifies these risks, allowing vulnerabilities to proliferate unchecked.
4. Container Vulnerabilities and Image Security: While containers play a pivotal role in CI/CD workflows, they are not immune to security threats. Vulnerabilities in container images—including outdated software versions, misconfigurations, or insecure base images—pose risks that can be exploited by malicious actors. Without rigorous scanning and validation, these weaknesses can propagate through the pipeline.
5. Misconfiguration of CI/CD Tools: Improperly configured CI/CD tools may leave workflows exposed to unauthorized access and inadvertently disclose sensitive code. Mismanagement of access control settings raises the potential for privilege escalation or code exposure. Additionally, hardcoded credentials and mismanaged environment variables create opportunities for attackers to extract crucial information, potentially leading to data breaches.
6. Supply Chain Attacks: Compromised third-party dependencies can introduce malicious packages and vulnerabilities into the pipeline. Unverified third-party tools or libraries can trigger widespread infection throughout the development cycle, especially when not adequately scrutinized.
7. Insider Threats: Insider threats can arise from authorized personnel, including developers, DevOps engineers, system administrators, or third-party contractors, who may intentionally or accidentally compromise the pipeline. Weak authentication mechanisms, insufficient access controls, and inadequate monitoring heighten the risk of unauthorized alterations, credential theft, or the insertion of malicious code into the workflow.
Enhancing CI/CD Workflow Security with Wazuh
Wazuh is an open-source security platform that provides unified Extended Detection and Response (XDR) and Security Information and Event Management (SIEM) capabilities for on-premises, containerized, virtualized, and cloud environments. This platform empowers organizations to implement security measures that address the challenges and mitigate risks associated with CI/CD workflows. Key enhancements provided by Wazuh include:
Log Collection and System Monitoring
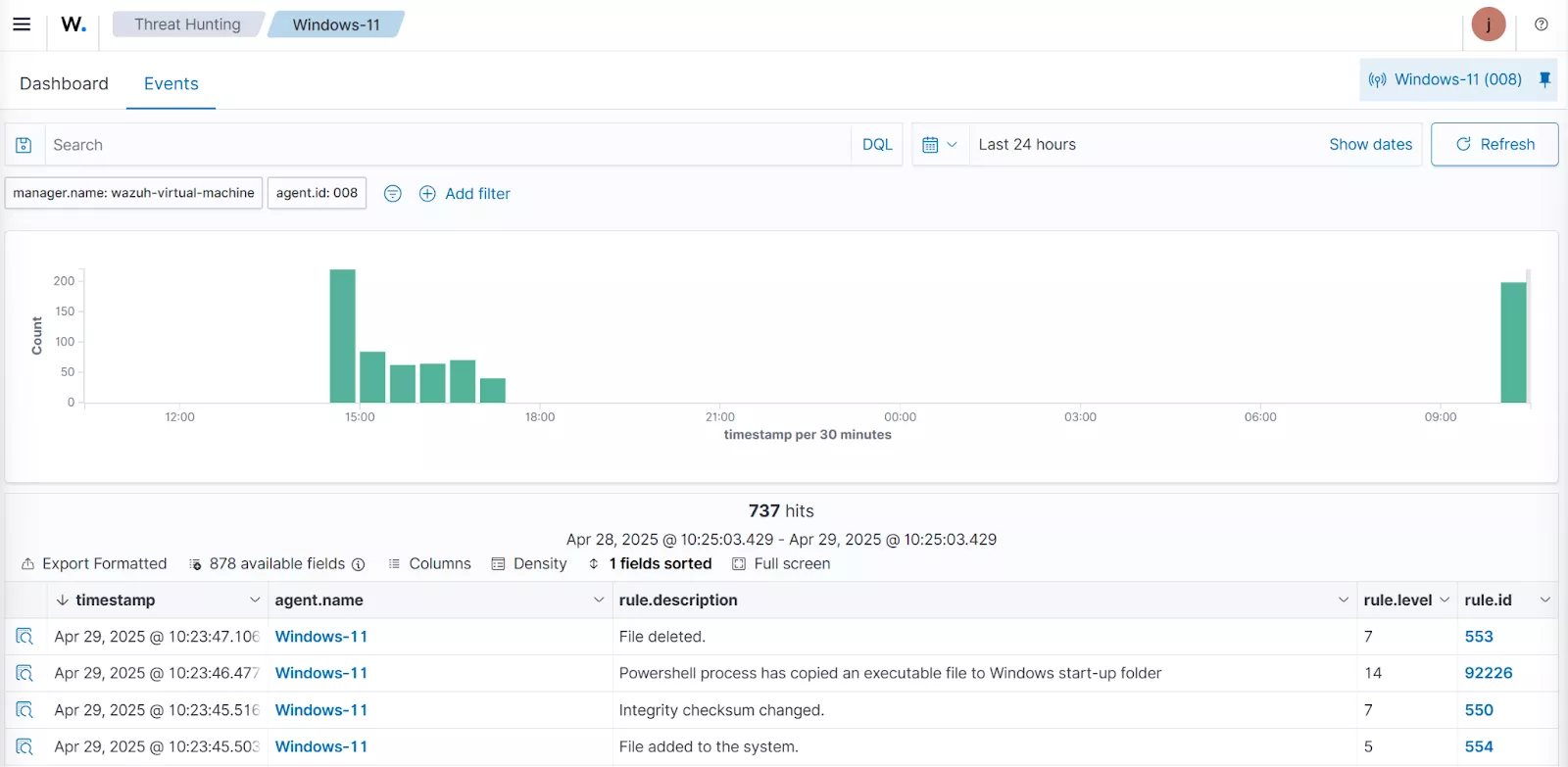
Wazuh offers comprehensive log collection and analysis capabilities to continually monitor the various components of the CI/CD environment for security threats. It aggregates and analyzes logs from crucial pipeline elements, including servers, containerization and orchestration tools like Docker and Kubernetes, and version control systems such as GitHub. This holistic monitoring allows security teams to identify unusual activities, unauthorized access, or potential security breaches within the CI/CD infrastructure.
Moreover, Wazuh’s File Integrity Monitoring (FIM) capability detect unauthorized modifications in code or configuration files. By monitoring files in real-time or via scheduled intervals, Wazuh generates alerts for security teams regarding file activities such as creation, deletion, or modification.
Custom Rules and Streamlined Security Monitoring
Wazuh empowers users to establish custom rules and alerts tailored to specific security requirements within their CI/CD pipelines. Organizations can define rules that align with their security protocols, enabling detailed monitoring of code changes, server configurations, or container images. This flexibility allows for the implementation of granular security controls that cater to individual organizational needs.
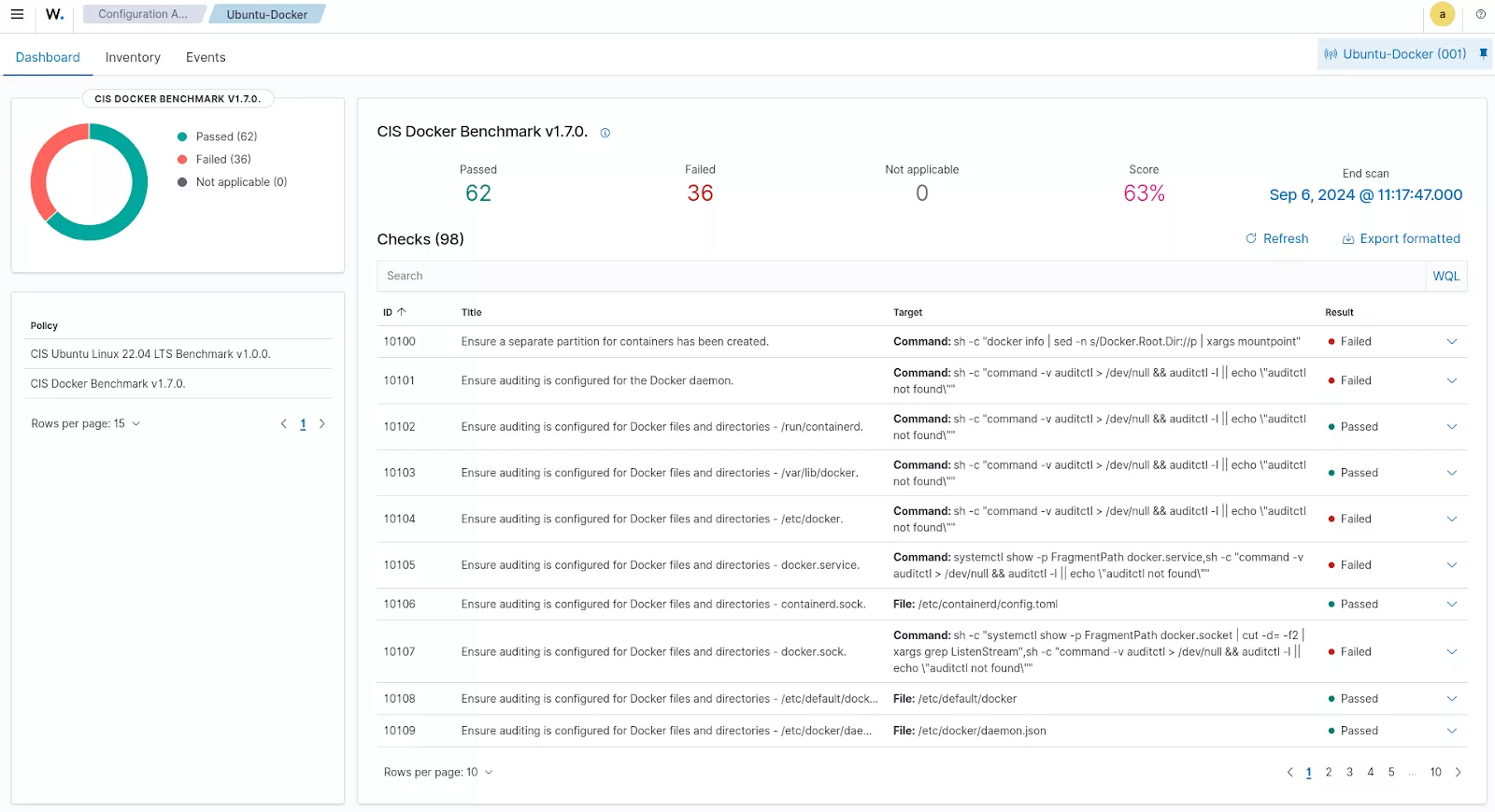
For example, the Center for Internet Security (CIS) Docker Benchmark provides best practices for securing Docker environments. Organizations can automate compliance checks against CIS Docker Benchmark v1.7.0 using the Wazuh Security Configuration Assessment (SCA) capability.
Integration with Third-Party Security Tools
Wazuh can seamlessly integrate with a variety of security tools and platforms, including container vulnerability scanners and CI/CD orchestration systems. This is particularly vital in CI/CD workflows, which often utilize multiple tools to manage different phases of the development lifecycle. By aggregating data from various sources, Wazuh provides a centralized overview of security proceedings throughout the pipeline.
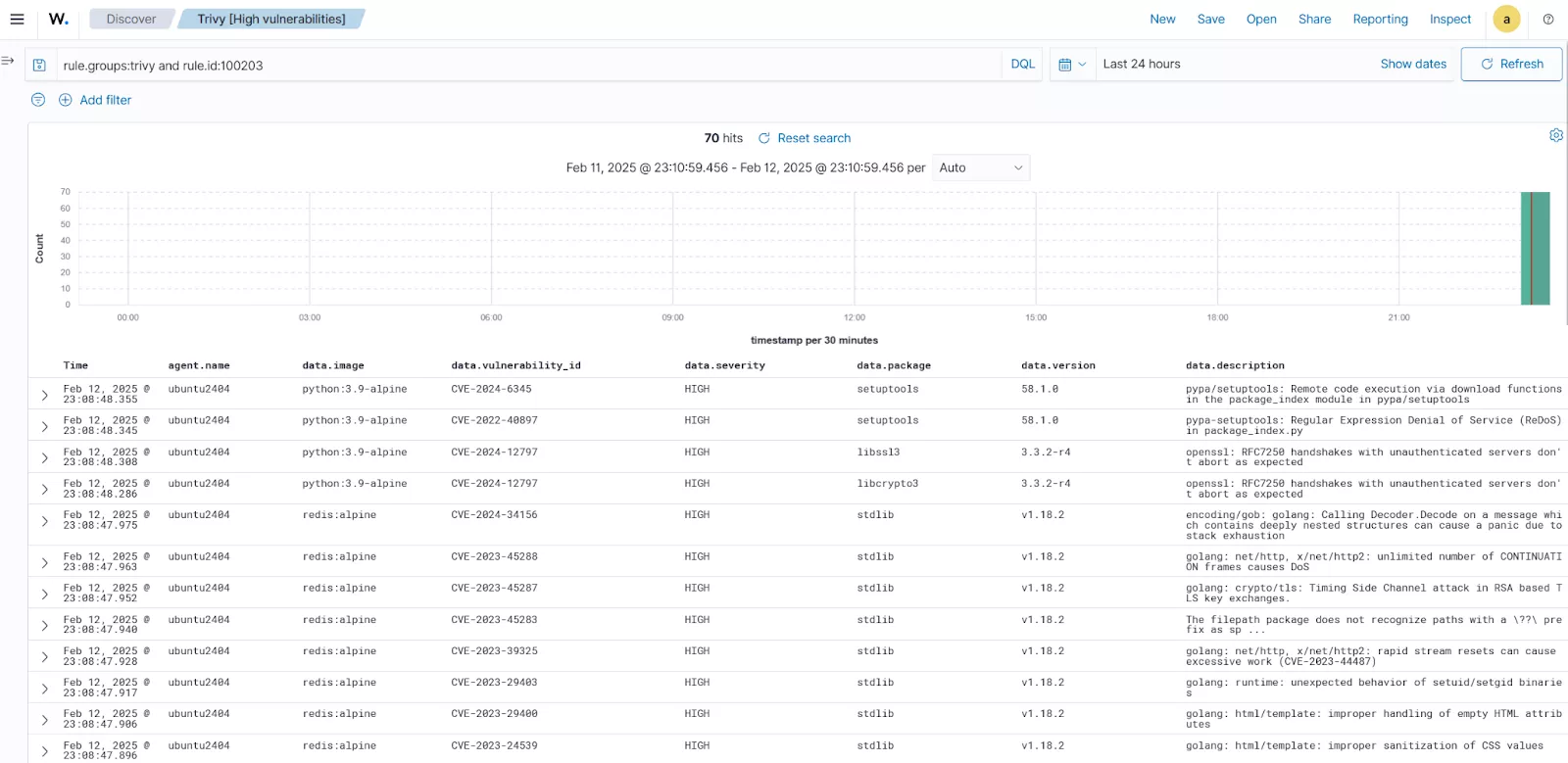
For instance, Wazuh integrates with container vulnerability scanning tools such as Trivy and Grype, which are used to scrutinize container images for vulnerabilities, insecure base images, or outdated software versions. By conducting scans of container images prior to their deployment in production, organizations can verify that only secure and updated images are used during deployment.
Automated Incident Response
Given the rapid pace of CI/CD workflows, it is imperative to identify and address threats swiftly to minimize the risk of breaches or downtime. Wazuh provides robust incident response capabilities that enable organizations to respond to security incidents promptly.
The Wazuh Active Response module can automatically execute remediation actions upon the detection of a security threat. For instance, if a malicious IP address is identified as attempting to access a system running CI/CD processes, Wazuh can automatically block the IP address and initiate predefined counteractions. This level of automation ensures rapid response times, reduces the necessity for manual intervention, and mitigates the potential escalation of security threats.
Conclusion
Securing CI/CD workflows is essential for maintaining a secure and reliable software development environment. By leveraging Wazuh, organizations can proactively identify vulnerabilities, monitor for security anomalies, enforce compliance, and automate security responses, all while preserving the speed and efficiency of CI/CD processes. Incorporating Wazuh into CI/CD workflows ensures that security measures keep pace with the development cycle, thereby strengthening overall security posture.