UN Introduces Comprehensive Cyber-Attack Assessment Framework
The United Nations has introduced a new cyber-attack assessment framework to complement existing cybersecurity models like the MITRE ATT&CK framework. The United Nations Institute for Disarmament Research (UNIDR) Intrusion Path framework is designed to analyze both malicious activities and security measures within the information and communication technology (ICT) landscape.
This framework aims to assist UN member states and non-technical stakeholders in understanding malicious IT activities, particularly in a landscape often dominated by complex terminology used in the technical community. The framework provides a more accessible overview of the various layers of IT networks where malicious actions can occur, thereby supporting more inclusive and informed cyber diplomacy.
As cyber threats within the ICT environment escalate, potentially endangering international peace and stability, it becomes essential to equip policymakers and other stakeholders with tools that foster comprehension and collaborative action towards creating a more transparent and stable digital domain. The UN has expressed hope that the UNIDIR Intrusion Path will facilitate these objectives.
The UNIDIR Intrusion Path model was effectively utilized in a research study published in December 2024, which explored the impact of artificial intelligence on the tactics and behaviors of both attackers and defenders navigating the different layers of the intrusion path.
Visualizing the Network Perimeter
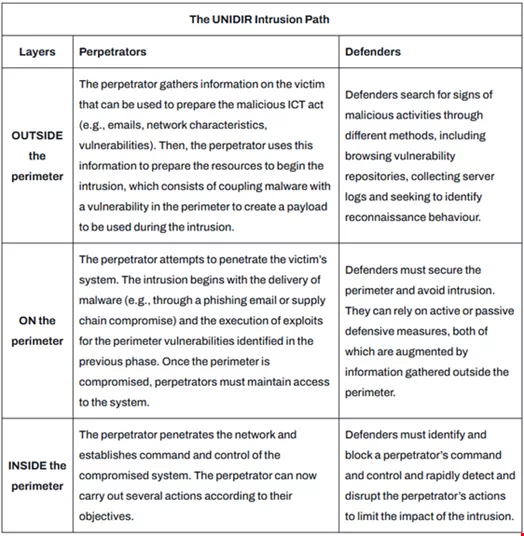
The framework is organized into three levels of analysis focusing on the concept of the network perimeter, specifically detailing activities outside the perimeter, on the perimeter, and inside the perimeter:
– Outside the Perimeter: Encompasses all systems, networks, and data sources situated beyond an organization’s direct control, such as public websites and the dark web.
– On the Perimeter: Represents the boundary that separates an organization’s internal systems from the external environment, incorporating security tools like firewalls and intrusion detection systems.
– Inside the Perimeter: Refers to the organization’s internal network, including subnetworks and devices that store sensitive data and operational systems.
The framework outlines the potential activities that perpetrators might leverage to breach system defenses across these layers and illustrates how defenders can monitor and prevent such intrusions.
The UNIDIR Intrusion Path framework is designed to complement two well-established tools in analyzing malicious ICT activities: the MITRE ATT&CK framework and the Cyber Kill Chain.
The MITRE ATT&CK framework, developed by the MITRE Corporation and launched in 2013, categorizes the tactics, techniques, and procedures employed by attackers throughout the various phases of an intrusion. Meanwhile, the Cyber Kill Chain, initiated by Lockheed Martin in 2011, outlines the sequential stages of a cyber-attack, ranging from initial reconnaissance to data exfiltration.
By integrating the UNIDIR Intrusion Path with these established models, stakeholders can gain a holistic understanding of cybersecurity dynamics, enabling them to implement more effective defense mechanisms against the escalating tide of cyber threats.








