Supply Chain Compromise Affects Gluestack NPM Packages with 960,000 Weekly Downloads

A significant supply chain compromise has occurred within the Node Package Manager (NPM) ecosystem, impacting 16 widely utilized Gluestack packages, specifically ‘react-native-aria’. These packages collectively account for over 950,000 downloads weekly and now contain malicious code that functions as a remote access trojan (RAT).
The attack was identified on June 6 at 4:33 PM EST, following the publication of a new version of the react-native-aria/focus package to NPM. Since this initial compromise, the threat actors have updated 16 out of the 20 Gluestack react-native-aria packages, with the latest version being released just two hours prior.
Source: BleepingComputer
This supply chain attack was uncovered by Aikido Security, which detected obfuscated code infiltrating the lib/index.js file across several affected packages:
| Package Name | Version | Weekly Downloads |
| react-native-aria/button | 0.2.11 | 51,000 |
| react-native-aria/checkbox | 0.2.11 | 81,000 |
| react-native-aria/combobox | 0.2.10 | 51,000 |
| react-native-aria/disclosure | 0.2.9 | 3 |
| react-native-aria/focus | 0.2.10 | 100,000 |
| react-native-aria/interactions | 0.2.17 | 125,000 |
| react-native-aria/listbox | 0.2.10 | 51,000 |
| react-native-aria/menu | 0.2.16 | 22,000 |
| react-native-aria/overlays | 0.3.16 | 96,000 |
| react-native-aria/radio | 0.2.14 | 78,000 |
| react-native-aria/switch | 0.2.5 | 477 |
| react-native-aria/toggle | 0.2.12 | 81,000 |
| react-native-aria/utils | 0.2.13 | 120,000 |
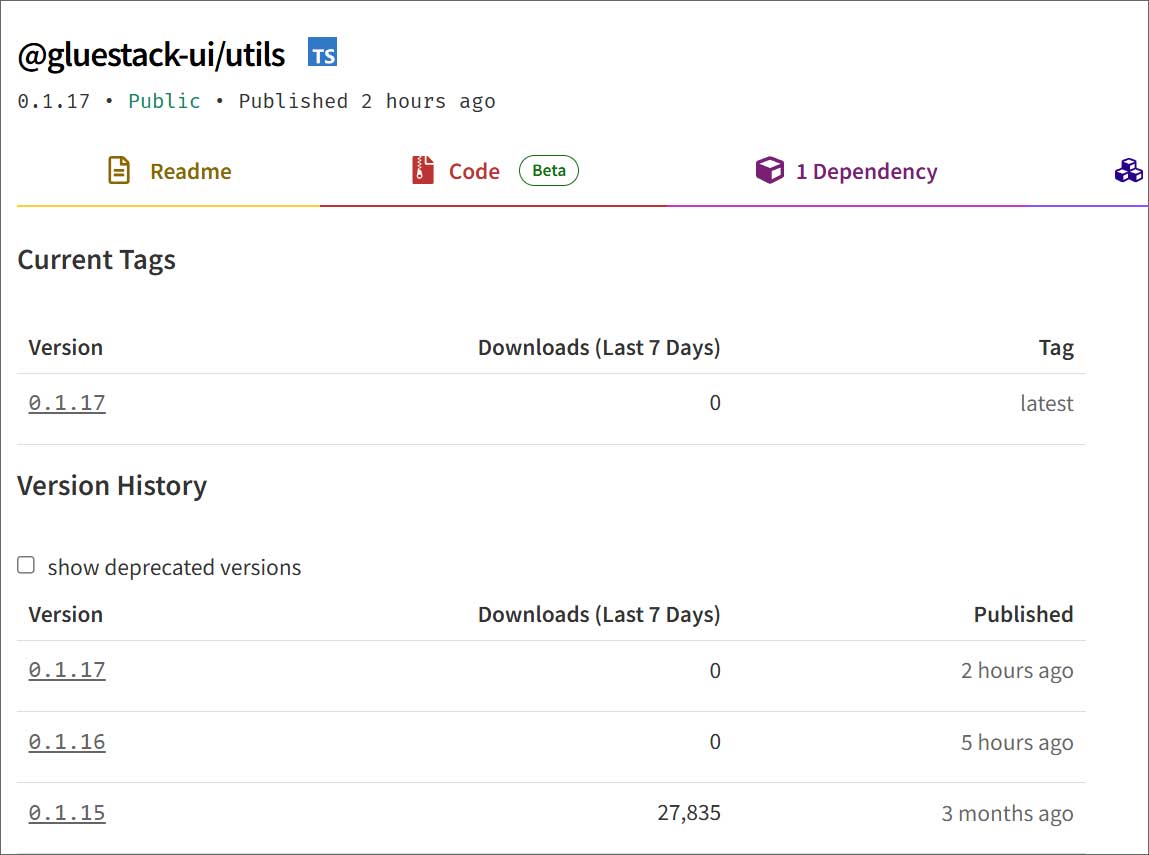
| gluestack-ui/utils | 0.1.17 | 55,000 |
| react-native-aria/separator | 0.2.7 | 65 |
| react-native-aria/slider | 0.2.13 | 51,000 |
Collectively, these packages are extensively used, with a striking total of approximately 960,000 weekly downloads, underscoring the potential widespread implications of this breach.
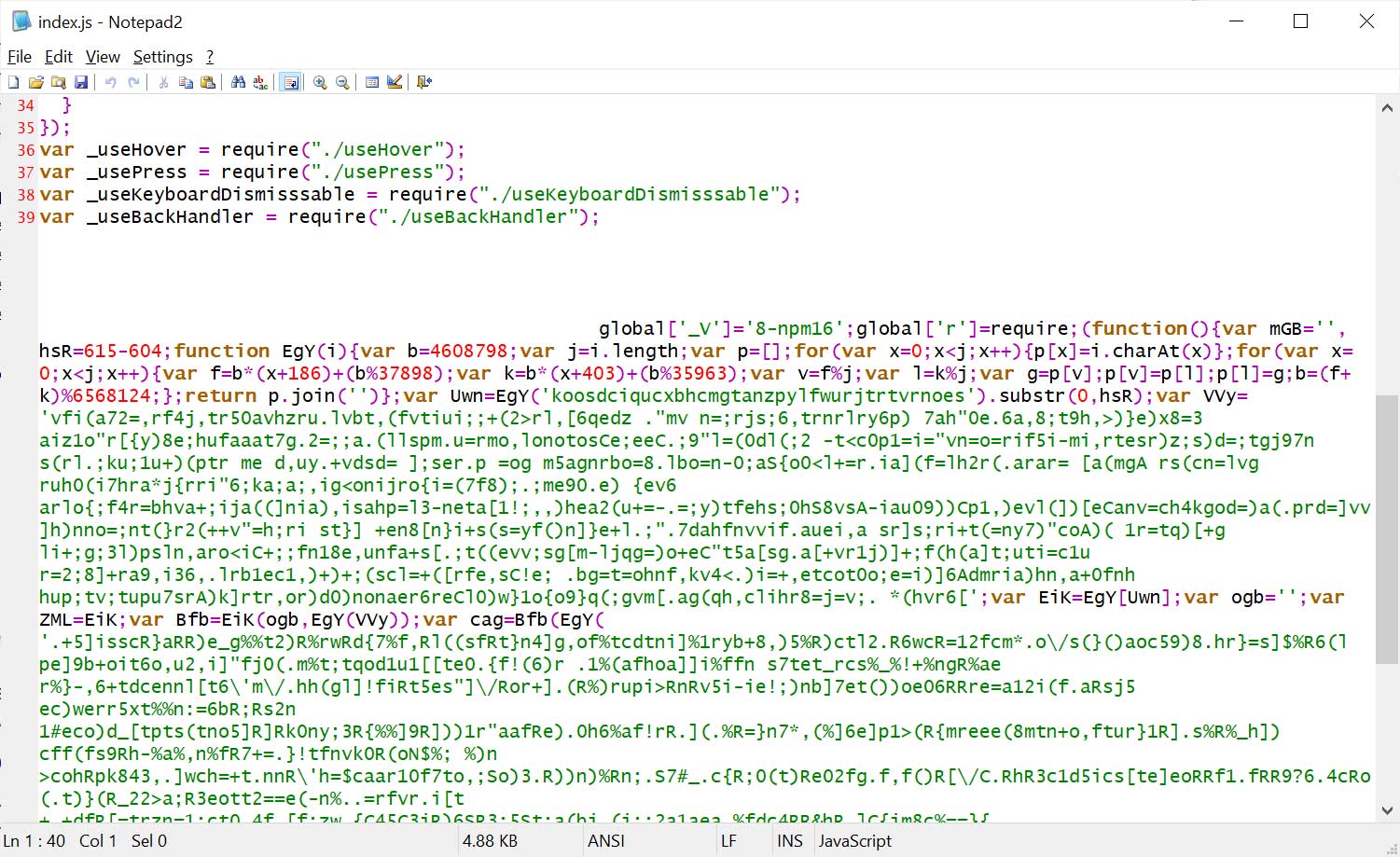
The obfuscation of the malicious code complicates its detection, as it is designed to blend within the legitimate code by being appended to the end of the index.js file, framed by excessive whitespace.
Source: BleepingComputer
Aikido’s findings indicate that this malicious code closely resembles a RAT associated with a previous NPM compromise identified the prior month.
The analysis of this earlier incident reveals that the RAT actively connects to an attacker-controlled command and control server, which enables the execution of remote commands.
Commands leveraged by the trojan include:
- cd – Change the current working directory
- ss_dir – Reset directory to the script’s path
- ss_fcd:
– Force change directory to - ss_upf:f,d – Upload a specific file f to a destination d
- ss_upd:d,dest – Upload all files from directory d to destination dest
- ss_stop – Set a flag to interrupt the current upload process
- Any other input – Treated as a shell command, executed via child_process.exec()
Additionally, the trojan facilitates Windows PATH hijacking by modifying the PATH environment variable to prepend a counterfeit Python path (%LOCALAPPDATA%ProgramsPythonPython3127). This enables the execution of malicious binaries under the guise of legitimate python or pip commands.
Researcher Charlie Eriksen from Aikido has made several attempts to communicate with Gluestack regarding the compromise through the issuance of GitHub issues on each relevant repository, but as of this moment, no response has been received.
“We have yet to receive a response from the package maintainers, which may be attributed to it being early on a Saturday morning in the US,” remarked Eriksen.
Aikido has also reported this incident to NPM and is currently awaiting their response, which typically involves several days for resolution.
Aikido attributes this attack to the same threat actors responsible for compromising four additional NPM packages earlier in the week, namely biatec-avm-gas-station, cputil-node, lfwfinance/sdk, and lfwfinance/sdk-dev.
Attempts to reach out to Gluestack for comments concerning the compromised packages have yielded no response to date.