Ransomware Groups Are Intensifying Their Use of Skitnet Post-Exploitation Malware

Ransomware groups are increasingly leveraging a sophisticated malware known as Skitnet, also referred to as “Bossnet,” to conduct stealthy post-exploitation operations within compromised networks.
This malware has been available for purchase on underground forums since April 2024. However, according to research conducted by Prodaft, it has gained notable traction among ransomware operations starting in early 2025.
Prodaft has reported observing numerous ransomware campaigns deploying Skitnet in actual attacks, including those conducted by BlackBasta utilizing Microsoft Teams phishing methods and other groups such as Cactus.

Source: Prodaft
Characteristics of Skitnet
The infection process initiated by Skitnet involves a Rust-based loader that is executed on the target system, decrypting a ChaCha20 encrypted binary written in Nim, which is subsequently loaded into memory.
This Nim payload creates a DNS-based reverse shell for communication with its command and control (C2) server, initiating sessions with randomized DNS queries.
The malware operates by launching three threads: one for sending heartbeat DNS requests, another for monitoring and exfiltrating shell output, and a third for receiving and decrypting commands from DNS responses.
Commands are relayed via HTTP or DNS, depending on the directives provided through the Skitnet C2 control panel. This interface allows operators to monitor the target’s IP address, geographical location, and operational status, as well as to issue commands for execution.
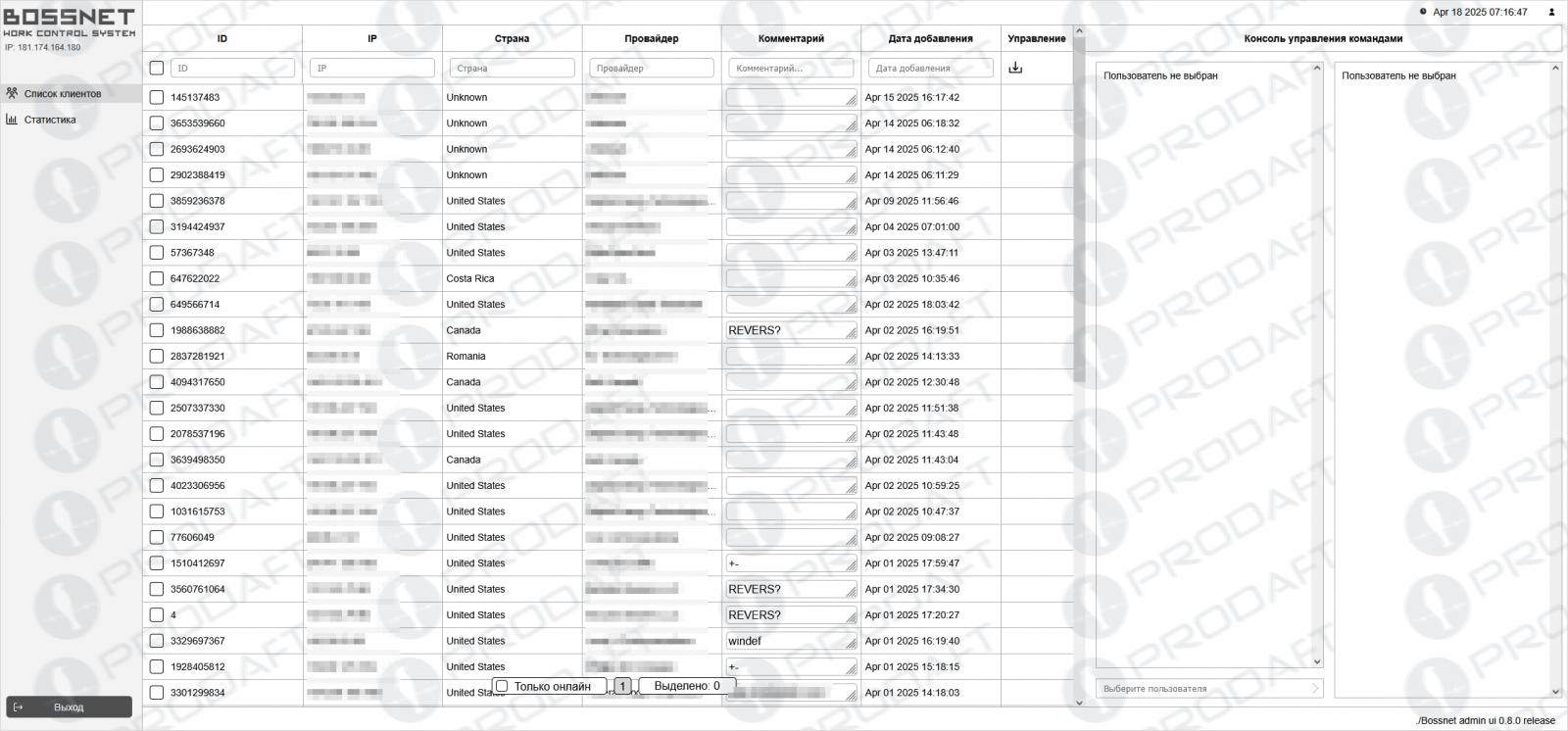
Source: Prodaft
The Skitnet C2 supports a range of commands that include:
- startup – This command establishes persistence by downloading three files, including a malicious DLL, and creating a shortcut to a legitimate Asus executable (ISP.exe) in the Startup folder. This initiates a DLL hijack that executes a PowerShell script (pas.ps1) for continuous C2 communication.
- Screen – It captures a screenshot of the victim’s desktop using PowerShell, uploads it to Imgur, and returns the image URL to the C2 server.
- Anydesk – Facilitates the silent download and installation of AnyDesk, a legitimate remote access tool, while concealing the window and notification tray icon.
- Rutserv – Enables the silent download and installation of RUT-Serv, another legitimate remote access tool.
- Shell – Starts a PowerShell command loop, initially sending a “Shell started…” notification, and then polling the server every five seconds for new commands to execute through Invoke-Expression, returning the results back.
- Av – Gathers information on installed antivirus and security software by querying WMI (SELECT * FROM AntiVirusProduct in the rootSecurityCenter2 namespace), sending this data to the C2 server.
Beyond the primary commands, operators can utilize a separate function involving a .NET loader to execute PowerShell scripts in memory, providing an even deeper level of customization for their attacks.
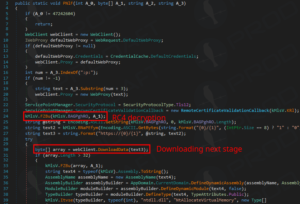
Source: Prodaft
While ransomware groups often develop custom tools specific to their operations, which tend to have low detection rates by antivirus solutions, the development of such tools can be resource-intensive and requires skilled developers who may not always be accessible, especially in smaller groups.
Employing off-the-shelf malware like Skitnet offers a cost-effective and swift deployment option while complicating attribution, as it is utilized by a diverse range of threat actors.
Within the ransomware landscape, both custom tools and off-the-shelf solutions coexist. However, the features offered by Skitnet render it particularly attractive to malicious actors.
Prodaft has released a set of indicators of compromise (IoCs) associated with Skitnet for public awareness. These can be found in their GitHub repository.








