North Korea Intensifies Cyber Espionage Activities in Ukraine to Evaluate Conflict Risks
The state-sponsored North Korean hacking group known as Konni (also referred to as Opal Sleet or TA406) has intensified its cyber espionage operations directed at Ukrainian governmental organizations. This strategic focus is believed to be part of a broader effort to gain intelligence regarding the ongoing conflict and the geopolitical landscape of the region.
The attackers employ phishing tactics, utilizing deceptive emails that mimic communications from think tanks. These messages reference significant political and military developments to entice recipients into engaging with malicious content.
Research conducted by Proofpoint, which identified this malicious activity in February 2025, infers that these cyber operations aim to assist North Korea’s military involvement alongside Russia in Ukraine. This intelligence gathering is geared towards understanding Ukrainian resilience against the Russian offensive and assessing the implications for the ongoing conflict.
According to Proofpoint, “TA406 is targeting Ukrainian government entities to gauge the willingness to sustain resistance against the Russian invasion and to evaluate the mid-term outlook of the hostilities.” North Korea’s commitment of troops to support Russia from late 2024 appears to drive this intelligence initiative, as it seeks insights into the conditions affecting its own deployed forces and potential escalations in military requests from Russia.
Attack Chain Analysis
The phishing emails are designed to impersonate individuals affiliated with fictitious think tanks, addressing critical issues such as the recent replacement of military leaders or impending presidential elections in Ukraine.
The attackers utilize various free email services, including Gmail, ProtonMail, and Outlook, to perpetuate the phishing campaign. These messages prompt the targets to click on links that lead to a MEGA-hosted download, which delivers a password-protected .RAR file onto the victim’s system. This file, named “Analytical Report.rar,” contains a similarly titled .CHM file.
Executing this .CHM file initiates embedded PowerShell scripts that extract reconnaissance data from the compromised host while establishing persistence within the environment. Proofpoint has observed adaptations of this attack that use HTML attachments to distribute ZIP archives, which may include harmless PDFs alongside malicious LNK files, facilitating further PowerShell and VBScript executions.
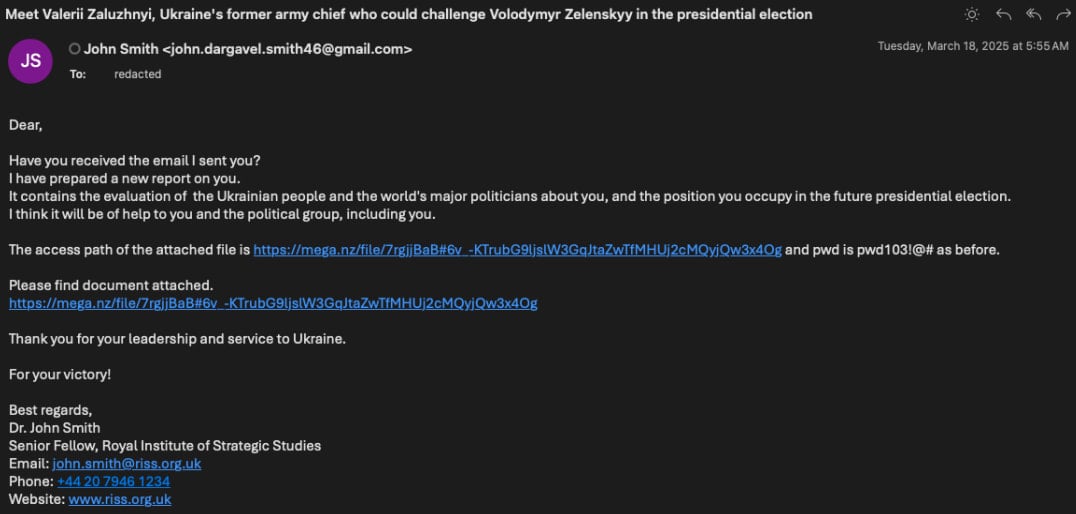
The culmination of these attacks is believed to involve malware or backdoor implementations meant to support ongoing espionage operations. However, specific details related to the final payload remain undisclosed.
Additionally, the researchers highlighted that prior attacks by Konni targeted the same demographic with the intention of harvesting credentials to compromise accounts. These preparatory measures involved emails masquerading as Microsoft security alerts, alerting recipients to perceived unusual sign-in activities and prompting them to verify their credentials via a phishing domain.
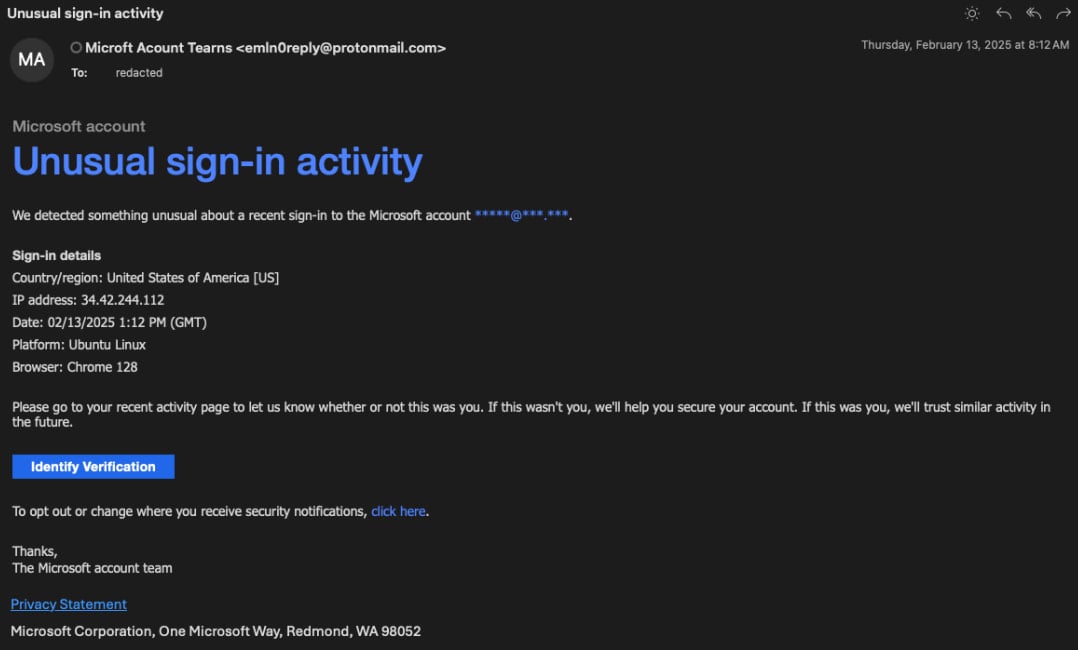
North Korea’s targeting of Ukrainian governmental bodies introduces a significant variable in the already intricate cybersecurity landscape, which has predominantly been characterized by relentless cyber offensives from Russian state-sponsored actors since the onset of the invasion.








