Graphite spyware Employed in Zero-Click iOS Attacks Targeting Journalists

Recent forensic investigations have validated the deployment of Paragon’s Graphite spyware platform in zero-click attacks against Apple iOS devices belonging to at least two journalists in Europe.
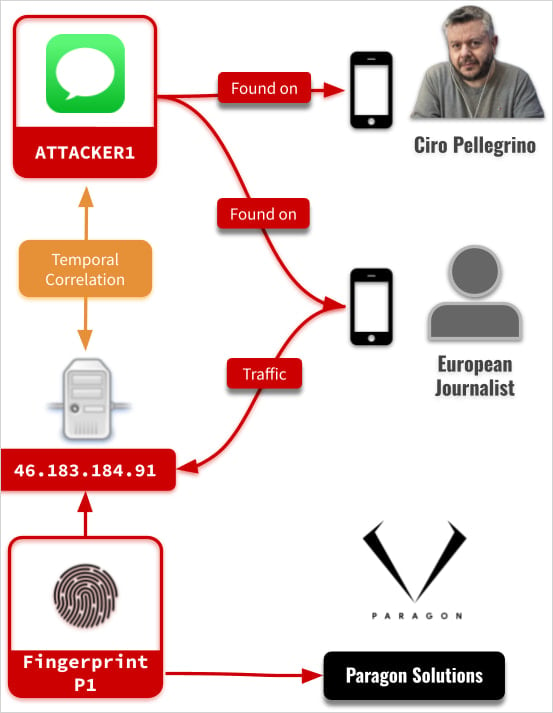
Citizen Lab researchers identified the targets as a prominent European journalist, who has opted for anonymity, and Ciro Pellegrino, a journalist from the Italian media outlet Fanpage.it.
The findings indicate with high confidence that both individuals were victims of Paragon’s Graphite mercenary spyware. The attacks were reported to have occurred in early 2025, with Apple notifying the victims on April 29 regarding their targeting by advanced spyware.
In these incidents, the threat actor employed Paragon’s Graphite spyware to target the iPhone devices running iOS 18.2.1, exploiting the zero-day vulnerability identified as CVE-2025-43200. Apple has described this vulnerability as a logic issue stemming from the processing of maliciously crafted photos or videos shared via iCloud Links.
The vulnerability was subsequently addressed in the subsequent iOS release, version 18.3.1, which included enhanced checks. The CVE identifier has been acknowledged in Apple’s security bulletin.
Citizen Lab’s analytical work indicates that the delivery mechanism for Graphite was through iMessage. The attacker, denoted in the research as ‘ATTACKER1’, sent specially crafted messages that utilized CVE-2025-43200 to execute remote code.
This method enabled the delivery of spyware without requiring any action from the targeted individuals, categorizing it as a zero-click attack, while also leaving no discernible evidence of tampering on the victims’ devices.
Once the spyware was executed, it established a connection to a command-and-control (C2) server for further operational directives. In the confirmed case by Citizen Lab, the compromised device connected to a VPS linked to Paragon’s infrastructure.
This particular server maintained operational status at least until April 12.
Source: Citizen Labs
Despite the limited traces left on the devices, Citizen Lab succeeded in retrieving logs that provided conclusive evidence, attributing the attacks to Paragon’s Graphite spyware with high certainty.
This spyware family was previously implicated in another zero-click attack earlier this year, which targeted other Italian victims by exploiting a zero-day vulnerability in WhatsApp.
Moreover, Italian authorities have confirmed multiple attacks against various individuals, including journalist Francesco Cancellato and activists Luca Casarini and Dr. Giuseppe “Beppe” Caccia. However, the identities of those responsible for these attacks remain unspecified.








