Google Associates Newly Discovered LostKeys Data Theft Malware with Russian Cyber Espionage Actors
Google Associates New LostKeys Malware with Russian Cyber Espionage
Since the beginning of 2025, the Russian state-backed ColdRiver hacking group has employed the newly identified LostKeys malware to conduct file theft in targeted espionage operations against Western entities, including governments, journalists, think tanks, and non-governmental organizations.
In December, United Kingdom and Five Eyes allies connected ColdRiver to Russia’s Federal Security Service (FSB), the nation’s primary agency for counterintelligence and internal security.
The Google Threat Intelligence Group (GTIG) first identified the deployment of LostKeys in January as part of ClickFix social engineering attacks, which involve tricking victims into executing malicious PowerShell scripts. The execution of these scripts allows for the download and execution of further PowerShell payloads, culminating in a Visual Basic Script (VBS) data theft malware referred to by Google as LostKeys.
GTIG noted, “LOSTKEYS is capable of stealing files from a predetermined list of extensions and directories, in addition to transmitting system information and active processes back to the attacker.” The research further elucidated that, “The typical modus operandi of ColdRiver is to first compromise credentials, which are subsequently used to access emails and contacts of the target. In select instances, they deploy malware known as SPICA to gain access to specific documents on the target system. LOSTKEYS is designed to achieve a similar objective and is used only in highly selective scenarios.”
ColdRiver is not the sole state-sponsored threat group utilizing ClickFix tactics; groups such as Kimsuky (North Korea), MuddyWater (Iran), APT28, and UNK_RemoteR (Russia) have similarly employed these methodologies in recent espionage activities.
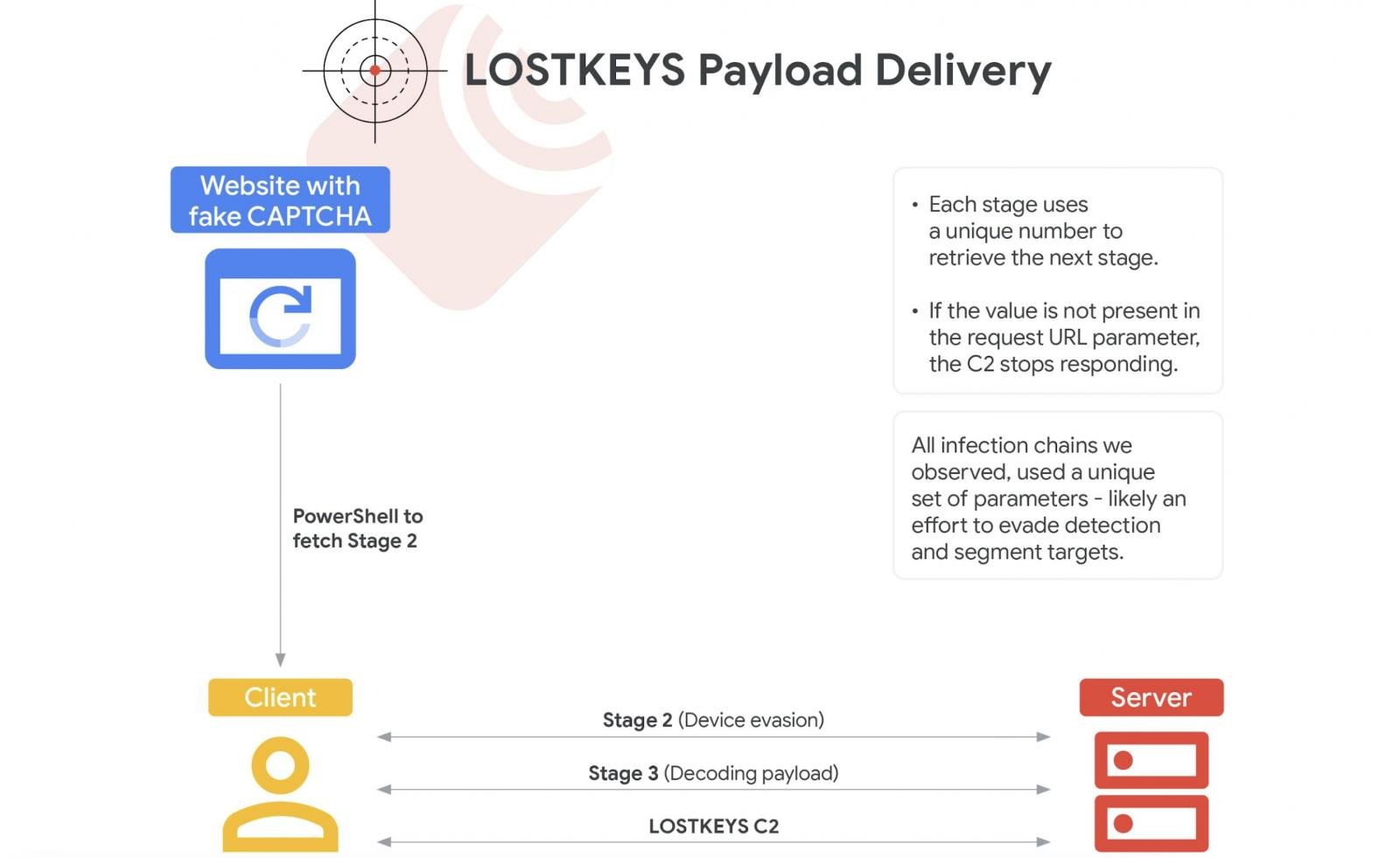
LostKeys attack flow (Google)
Also known as Star Blizzard, Callisto Group, and Seaborgium, the ColdRiver group has leveraged social engineering and open-source intelligence (OSINT) techniques to research and entrap targets since at least 2017. In December 2023, Five Eyes cyber agencies cautioned against ColdRiver’s spear-phishing operations aimed at defense and governmental organizations, NGOs, and politicians, which escalated following Russia’s invasion of Ukraine, extending to defense-industrial targets and U.S. Department of Energy facilities.
In 2022, the Microsoft Threat Intelligence Center (MSTIC) successfully disrupted a ColdRiver social engineering operation, wherein the attackers employed Microsoft accounts to harvest emails and monitor activities of organizations and high-profile individuals in NATO-affiliated countries.
In December 2023, the U.S. State Department imposed sanctions on two operators associated with ColdRiver, one of whom was an officer in the FSB, following their indictment by the U.S. Justice Department for participation in a globally coordinated hacking campaign orchestrated by the Russian government.
To further disrupt Russian cyber activities, the State Department has announced a reward of up to $10 million for information that may assist law enforcement in identifying or locating other members of ColdRiver.








