FBI Report: BADBOX 2.0 Android Malware Compromises Millions of Consumer Devices

The FBI has issued a warning regarding the BADBOX 2.0 malware, which has successfully infected over one million Internet-connected consumer devices. This malware campaign is transforming everyday electronics into residential proxies, facilitating various malicious activities.
The BADBOX botnet primarily targets a range of Chinese Android-based smart devices, including smart TVs, streaming boxes, projectors, tablets, and other Internet of Things (IoT) devices.
The FBI alerts that “the BADBOX 2.0 botnet comprises millions of compromised devices and features multiple backdoors to proxy services. Cybercriminals exploit these vulnerabilities, either by selling access or providing free services to hijacked home networks for nefarious purposes.”
Devices may come pre-installed with the BADBOX 2.0 malware or become infected through firmware updates and malicious applications that infiltrate Google Play and other app stores.
According to the FBI, unauthorized access to home networks may occur through two methods: pre-configuring the product with malicious software before purchase or infecting the device during the downloading of necessary applications containing backdoors, typically during initial setup.
Once integrated within home networks, these compromised IoT devices can be incorporated into the BADBOX 2.0 botnet and serve as residential proxy services exploited for unlawful activities.
Infected devices establish connections with the attackers’ command and control (C2) servers, where they receive directives to perform operations, including:
- Residential Proxy Networks: Traffic from cybercriminals is routed through victims’ home IP addresses, concealing their malicious activities.
- Ad Fraud: BADBOX is capable of generating ad revenue for threat actors by loading and clicking on ads in the background.
- Credential Stuffing: Utilizing victim IP addresses, attackers may attempt to gain unauthorized access to accounts using stolen credentials.
BADBOX 2.0 emerged as an evolution of the original BADBOX malware, identified in 2023 when it was found pre-installed on low-cost, lesser-known Android TV boxes such as the T95.
Throughout the following years, the malware’s botnet expanded. In 2024, Germany’s cybersecurity agency successfully disrupted the botnet by sinkholing communications between infected devices and the attackers’ infrastructure, thereby neutralizing the malware’s effectiveness.
Despite this disruption, the threat persisted, as researchers discovered the malware on 192,000 devices just a week later, including on more mainstream devices such as Yandex TVs and Hisense smartphones.
Alarming reports indicate that the botnet continued to proliferate, with HUMAN’s Satori Threat Intelligence estimating that over one million consumer devices had been compromised by March 2025.
This newly expanded botnet is now referred to as BADBOX 2.0, signifying an ongoing evolution in the malware campaign.
According to experts from HUMAN, “This scheme has affected over one million consumer devices. The types of devices connecting to the BADBOX 2.0 operation encompass budget ‘off brand’ products, uncertified tablets, connected TV boxes, digital projectors, among others.”
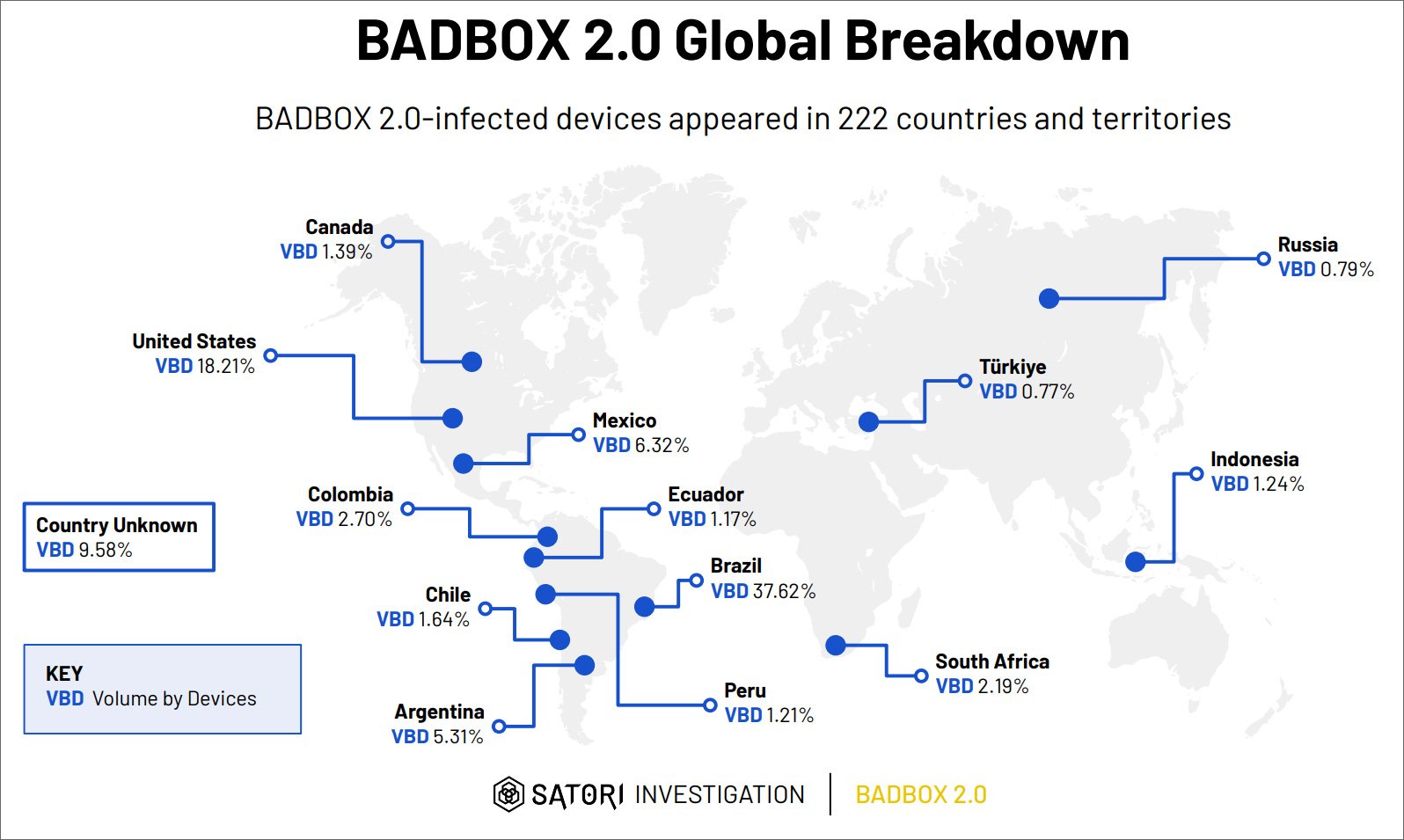
Additionally, “the infected devices are those using the Android Open Source Project, not those running the Android TV OS or certified as Play Protect compliant. All affected devices are manufactured in mainland China and distributed worldwide, with BADBOX 2.0-associated traffic observed from 222 countries and territories globally.”
Research indicates that the BADBOX 2.0 botnet spans 222 countries, with the largest concentrations of compromised devices in Brazil (37.6%), the United States (18.2%), Mexico (6.3%), and Argentina (5.3%).
Source: HUMAN Satori
In a collaborative endeavor led by HUMAN’s Satori team and partners including Google, Trend Micro, and The Shadowserver Foundation, additional disruptions to the BADBOX 2.0 botnet were carried out, severing communication for over 500,000 infected devices with the attackers’ servers.
Nonetheless, the botnet’s size continues to increase as consumers inadvertently connect more compromised devices to the Internet.
Identified devices affected by the BADBOX malware include:
| Device Model | Device Model | Device Model | Device Model |
| TV98 | X96QMaxP | Q96L2 | X96Q2 |
| X96mini | S168 | ums5121h10Natv | X96_S400 |
| X96mini_RP | TX3mini | HY-001 | MX10PRO |
| X96mini_Plus1 | LongTV_GN7501E | Xtv77 | NETBOX_B68 |
| X96Q_PR01 | AV-M9 | ADT-3 | OCBN |
| X96MATE_PLUS | KM1 | X96Q_PRO | Projector_T6P |
| X96QPRO-TM | sp7731e1h10native | M8SPROW | TV008 |
| X96Mini_5G | Q96MAX | Orbsmart_TR43 | Z6 |
| TVBOX | Smart | KM9PRO | A15 |
| Transpeed | KM7 | iSinbox | I96 |
| SMART_TV | Fujicom-SmartTV | MXQ9PRO | MBOX |
| X96Q | isinbox | Mbox | R11 |
| GameBox | KM6 | X96Max_Plus2 | TV007 |
| Q9 Stick | SP7731E | H6 | X88 |
| X98K | TXCZ |
Symptoms suggesting a BADBOX 2.0 infection include the presence of suspicious app marketplaces, disabled Google Play Protect settings, advertisements for streaming devices claiming to be unlocked or offering free content access, and detections of unusual Internet traffic.
The FBI recommends consumers take proactive measures to shield themselves from this botnet by adhering to the following protocols:
- Evaluate all IoT devices linked to home networks for irregular behavior.
- Avoid downloading applications from unofficial marketplaces promoting “free streaming” content.
- Monitor Internet traffic to and from home networks vigilantly.
- Ensure all household devices are updated with the latest software patches and updates.
If you suspect that your device has been compromised, it is critical to isolate it from the network and restrict its Internet access to disrupt the malware’s functionality.








