Emerging ClickFix Attacks on Linux Systems Under Investigation by Cybersecurity Experts
A recent campaign utilizing ClickFix attacks has been identified, specifically targeting Linux systems alongside traditional Windows environments. ClickFix represents a social engineering method that exploits false verification systems or application errors, coercing users into executing console commands that result in malware installation.
Historically, ClickFix has predominantly focused on Windows targets, prompting users to initiate PowerShell scripts via the Windows Run command. This exploitation has led to widespread infections by info-stealer malware and ransomware. However, a recent campaign in 2024, which employed deceptive Google Meet error messages, successfully extended its reach to macOS users.
ClickFix Targeting Linux Users
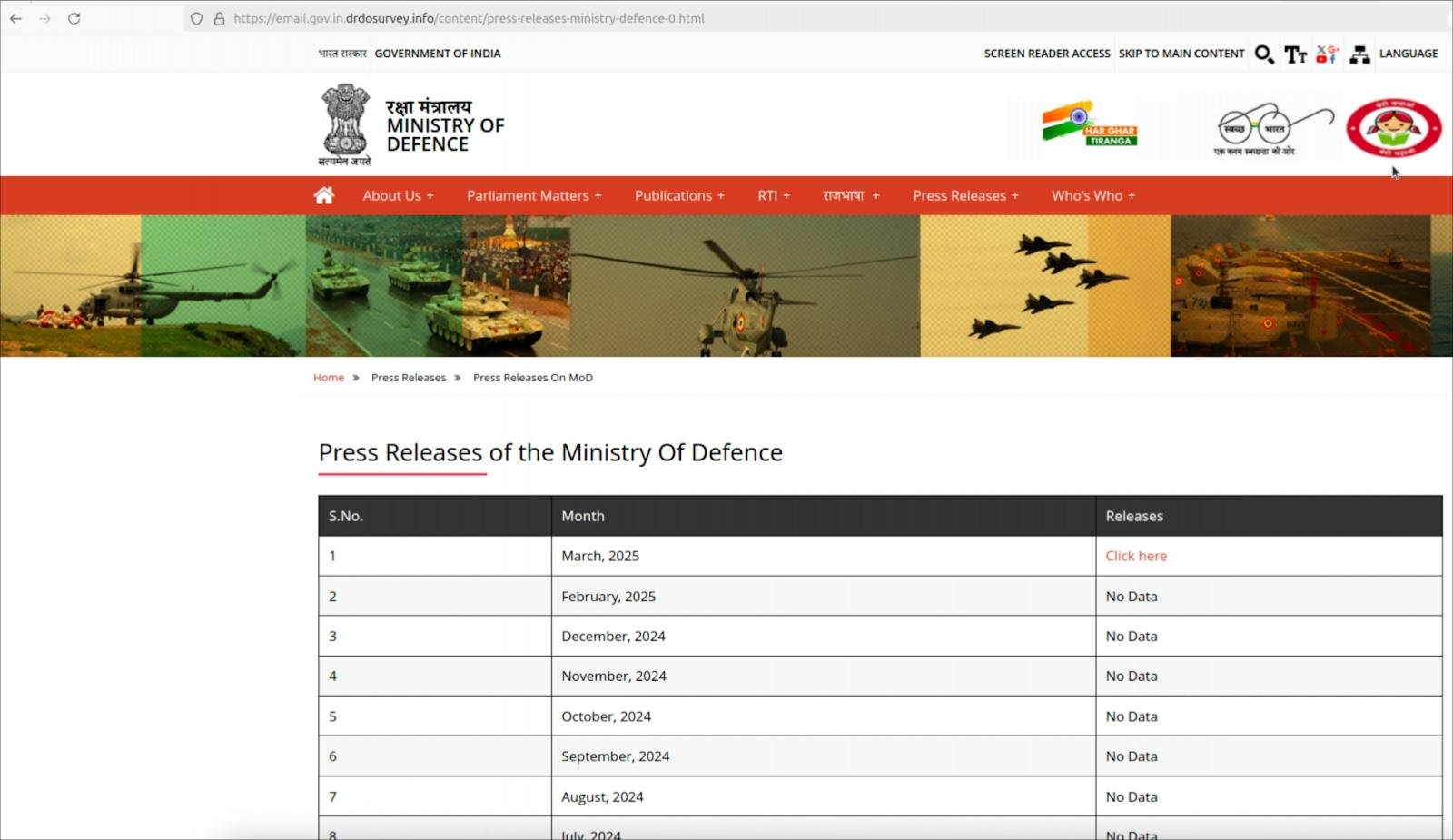
Researchers at Hunt.io have recently uncovered a campaign that marks one of the first adaptations of this social engineering tactic to Linux systems. This operation, attributed to the Pakistan-based threat group APT36 (also known as “Transparent Tribe”), features a website that impersonates the Indian Ministry of Defence and provides links to what is purportedly an official press release.
Visitors to this malicious website are profiled to ascertain their operating system before being redirected to an appropriate attack flow.
For Windows users, the attack manifests as a full-screen warning regarding restricted content usage rights. By clicking ‘Continue’, a JavaScript command is copied to the clipboard, prompting the user to paste and execute it in the Windows terminal. This activates a .NET-based loader which establishes a connection to the attacker’s server, while a decoy PDF is displayed to create an illusion of legitimacy.
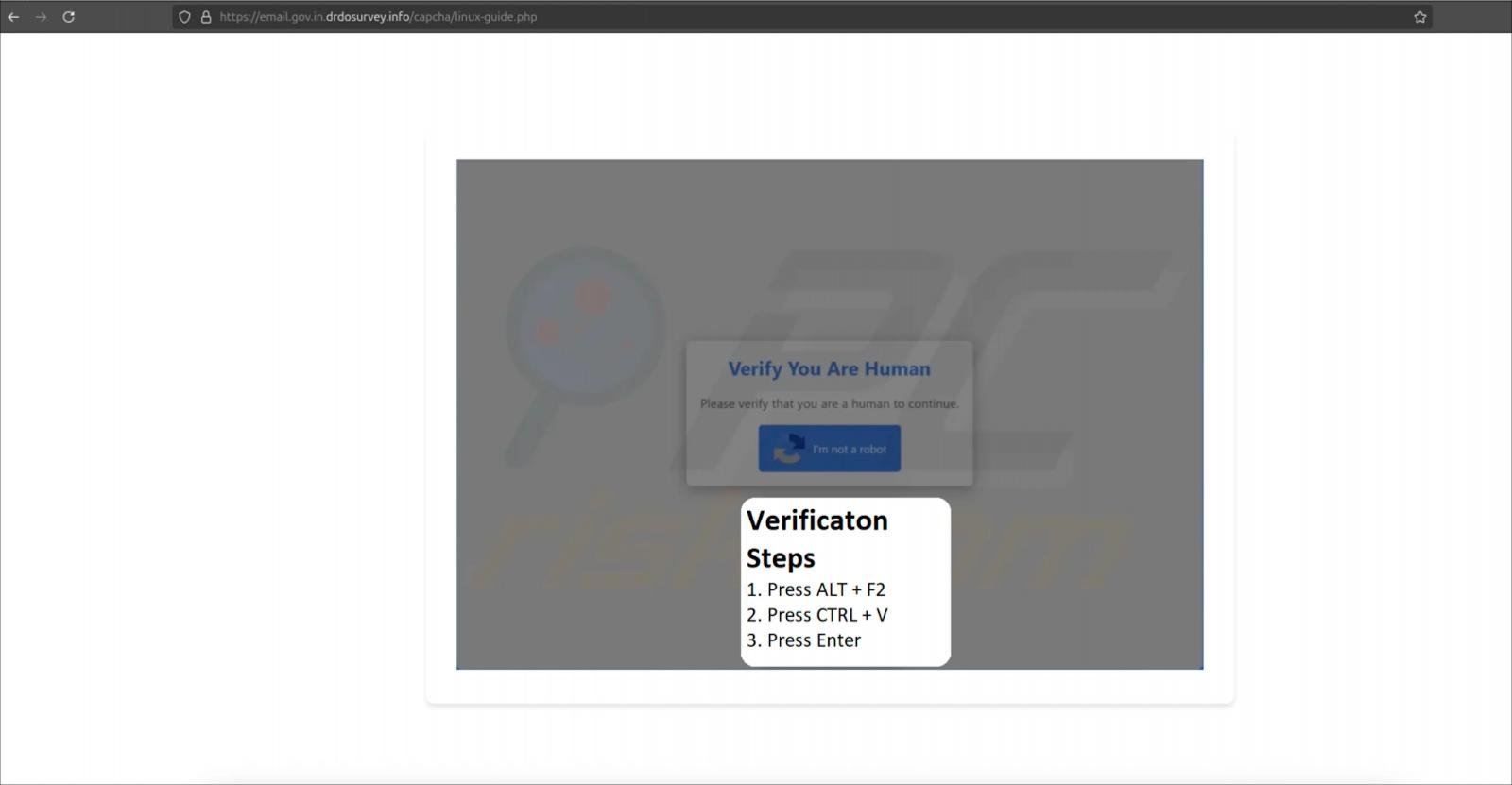
On the Linux front, users are redirected to a CAPTCHA page where clicking the “I’m not a robot” button leads to a shell command being copied to their clipboard. Victims are then guided to initiate the Linux run dialog with the combination ALT+F2, where they paste the command and press Enter.
This command facilitates the download of a payload named ‘mapeal.sh’ to the user’s system. According to Hunt.io’s analysis, the current version of this script does not perform any malicious actions—it merely retrieves a JPEG image from the attacker’s server.
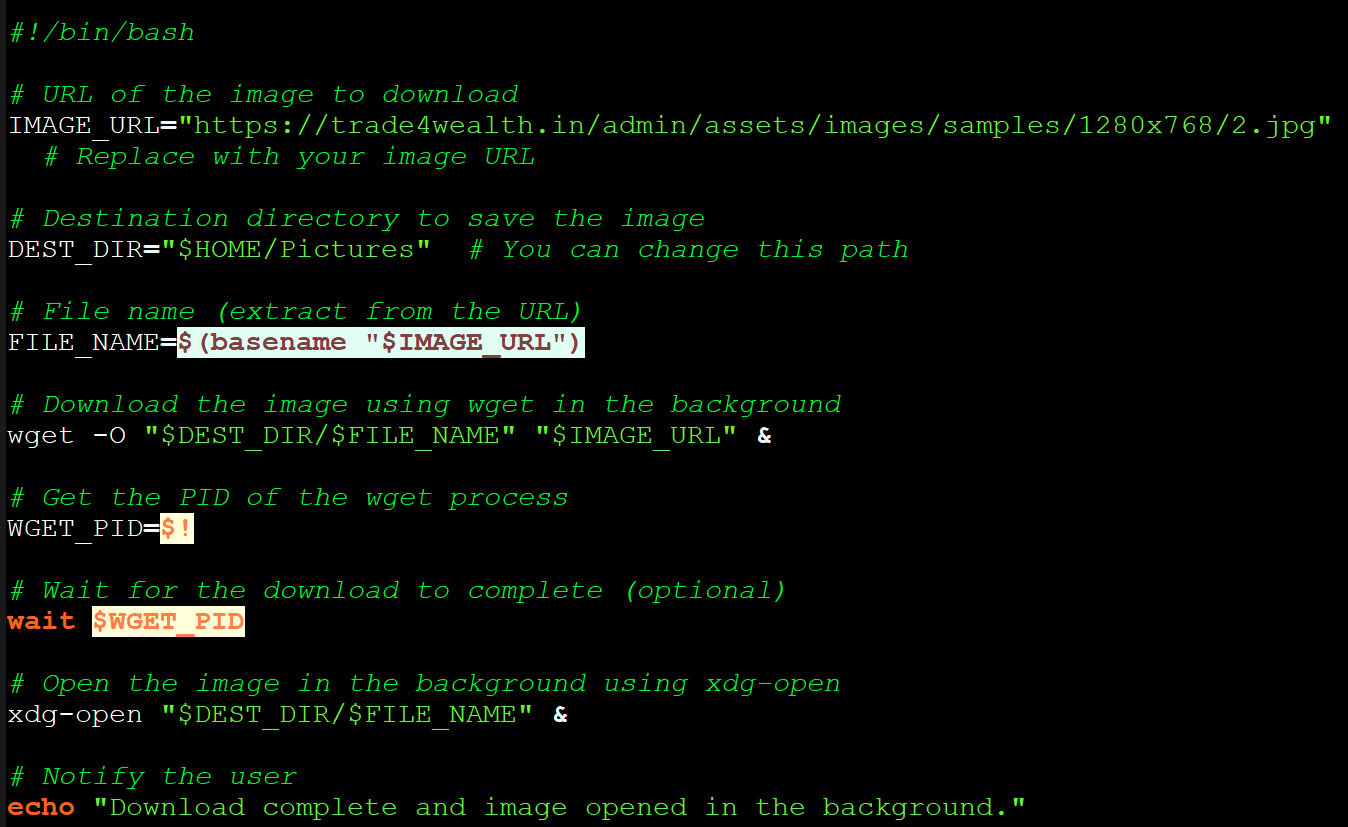
The retrieved image is opened in the background, and Hunt.io notes that no additional malicious activities—such as persistence mechanisms or lateral movement—were observed during its execution. Nonetheless, it is plausible that APT36 is experimenting with the Linux infection chain, as the underlying mechanism for infection could easily be adapted by substituting the image with a malicious shell script.
The successful extension of ClickFix to target Linux environments underscores its versatility, demonstrating that this attack vector is applicable across all major desktop operating systems.
In light of these developments, it is critical for users to exercise caution and avoid executing commands in run dialogs without fully understanding their implications. This practice significantly mitigates the risk of malware infection and unauthorized access to sensitive information.








