Emergence of Advanced ‘Fake Interview’ Schemes Utilizing 35 npm Packages for Malware Distribution

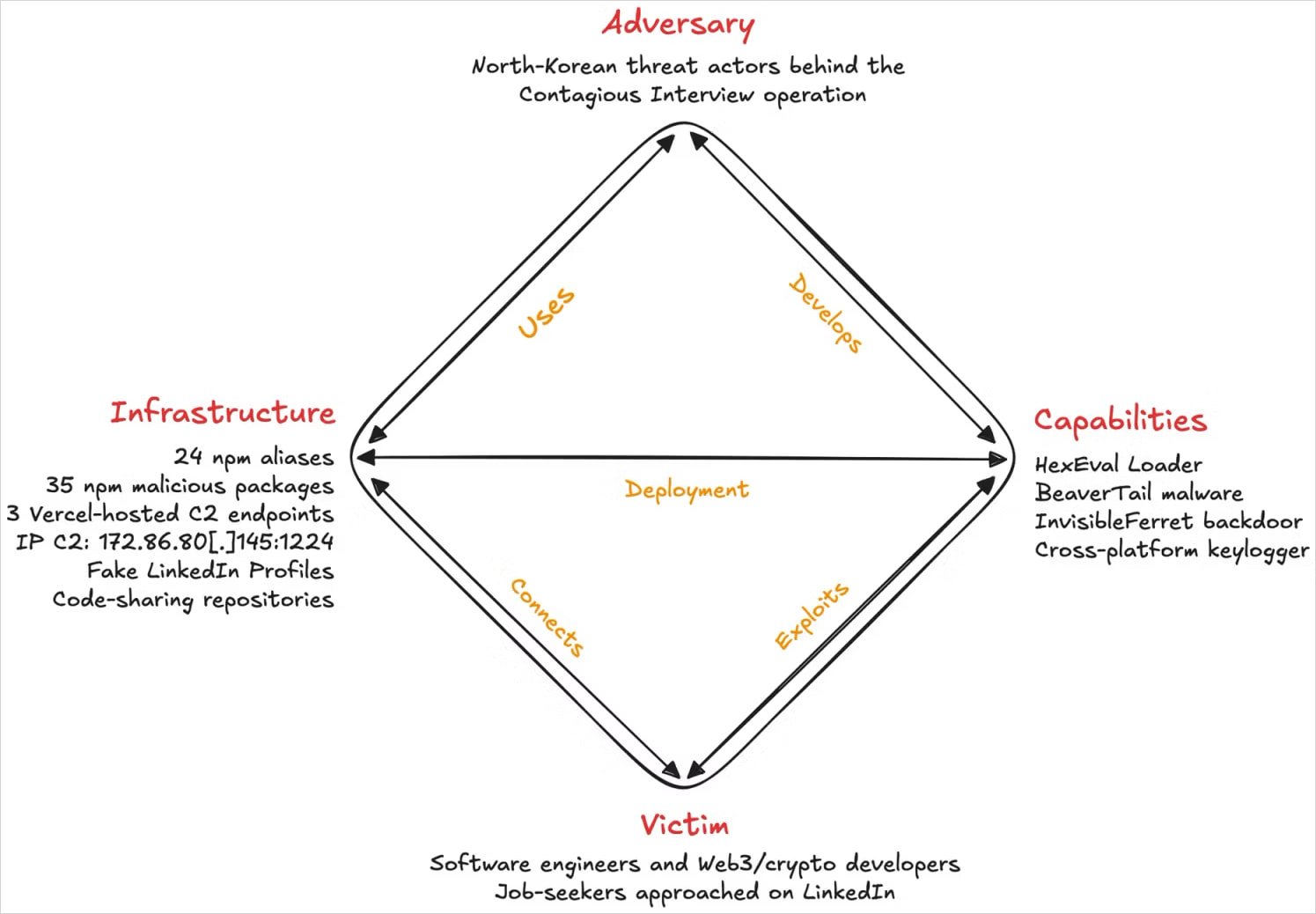
The recent resurgence of North Korea’s ‘Contagious Interview’ campaign has emerged as a significant threat, targeting job seekers through malicious npm packages designed to compromise developers’ devices. These packages facilitate the installation of information-stealing software and backdoors, heightening the risk for those in the software engineering field.
Research from a security firm reveals that 35 malicious packages were identified, submitted under 24 separate accounts. These packages have been downloaded over 4,000 times collectively, with six still accessible at the time of this report.
A disturbing characteristic of these malicious npm packages is their tendency to typosquat or imitate established and trusted libraries, which increases their potential for damage.
Among the notable imitation packages are:
- react-plaid-sdk, reactbootstraps
- vite-plugin-next-refresh, vite-loader-svg
- node-orm-mongoose
- jsonpacks, jsonspecific
- chalk-config
- node-loggers, *-logger
- framer-motion-ext
- nextjs-insight
- struct-logger, logbin-nodejs
Targets, mainly software engineers and developers, are approached by North Korean operatives masquerading as recruitment professionals. These operatives encourage candidates to download malicious packages embedded within coding “assignments” sent through platforms like Google Docs.
According to security analysts, “By impersonating recruiters on platforms such as LinkedIn, these threat actors share coding tasks and persuade candidates to execute the code outside of controlled environments, often using screen-sharing methods.” This manipulation leads to a series of infections that deploy multiple payloads on the victim’s system.
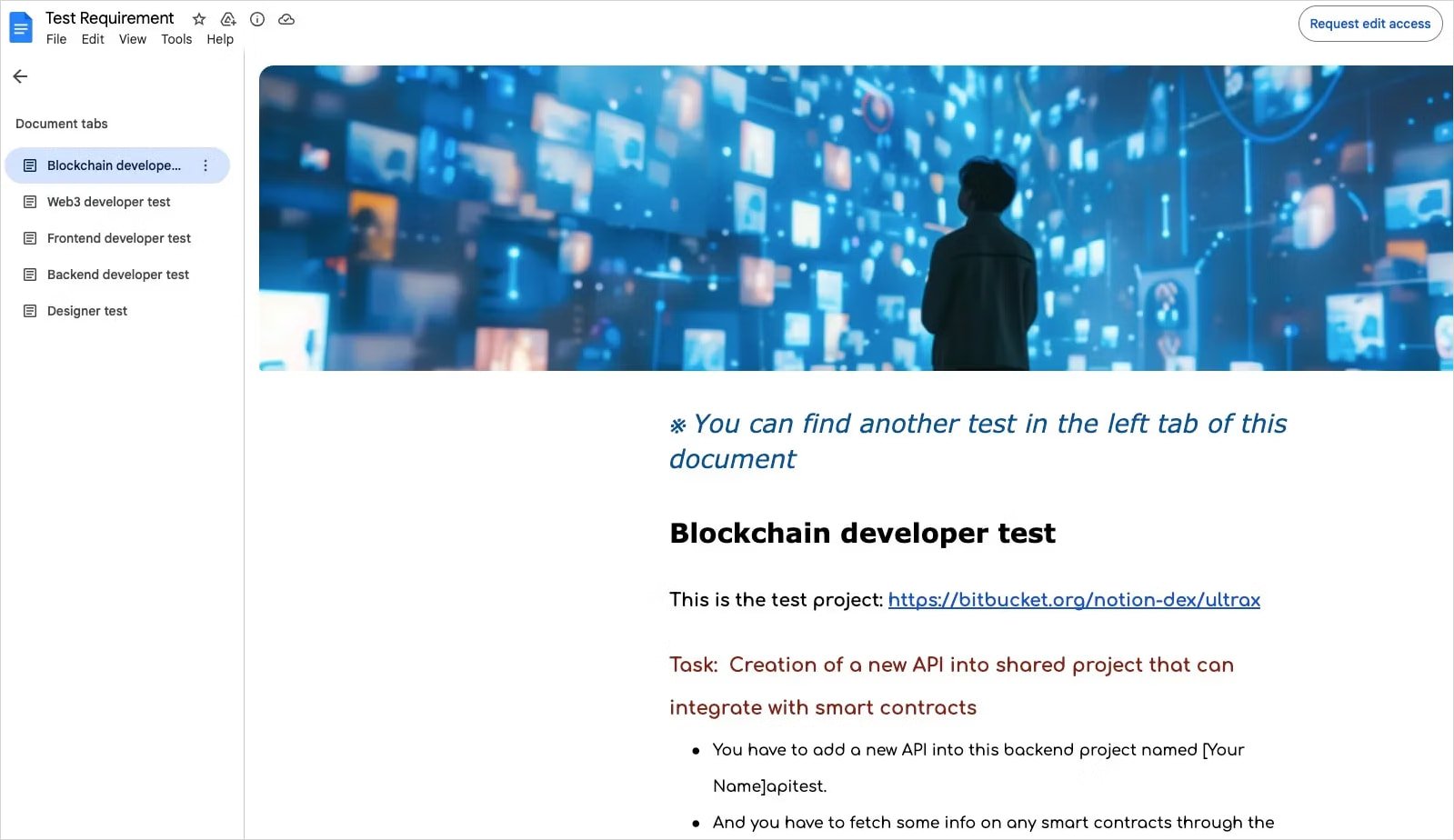
These assignments, which are hosted on platforms like Bitbucket, are cloaked as legitimate tasks but are structured to initiate a malicious payload chain. The initial step involves a loader concealed in the npm packages, which identifies the system, connects to the command-and-control (C2) server operated by the attackers, and utilizes the ‘eval()’ function to retrieve and execute the primary payload, known as BeaverTail.
BeaverTail functions as a cross-platform info-stealer and malware loader, designed to extract sensitive information such as browser data, cookies, and cryptocurrency wallet details. Subsequently, this malware initiates the deployment of the InvisibleFerret exploit.
InvisibleFerret is a persistent backdoor that allows attackers extended access to the compromised system. Delivered in a zipped format, it provides capabilities for remote control, file theft, and screen capture.
To conclude the attack, a cross-platform keylogger is also dropped, enabling real-time surveillance by monitoring input events and exfiltrating data. This keylogger is associated with only one of the npm aliases in this operation, indicating it may target specific high-value individuals.
Software developers presented with enticing remote job offers should exercise extreme caution. It is advisable to run any unknown code within isolated environments, such as containers or virtual machines, rather than executing them on production systems.
This is not the first instance of such tactics, with similar campaigns observed as recently as March, emphasizing the ongoing risk posed by North Korean threat actors.