Discord Vulnerability Enables Malicious Actors to Reutilize Expired Invitations in Cybersecurity Threat Campaigns

Recently discovered vulnerabilities in Discord’s invitation system are being exploited by cybercriminals to redirect users from expired or deleted invite links to malicious sites, where they download remote access trojans and information-stealing malware.
This malware delivery campaign capitalizes on a flaw within Discord’s infrastructure that facilitates multi-stage infection processes, successfully evading detection from several antivirus solutions.
Exploiting Expired Discord Invites
Discord invites enable users to join specific servers through URLs containing unique invite codes. These codes may be temporary, permanent, or customized for servers that have achieved ‘Level 3’ status by paying for exclusive perks. In regular servers, random invite links are generated, making repetitions highly unlikely.
Attackers have identified a critical loophole: when a Level 3 server loses its boost status, its unique invite code can be reused by different servers. This also applies to expired temporary or deleted permanent invites, as outlined by researchers at Check Point.
According to their findings, “the mechanism for creating custom invite links surprisingly lets you reuse expired temporary invite codes, and, in some cases, deleted permanent invite codes.”
Moreover, the flawed system does not update the expiration of previously generated temporary invitation codes when they are reused as permanent links. This miscommunication has facilitated the attackers’ activities.
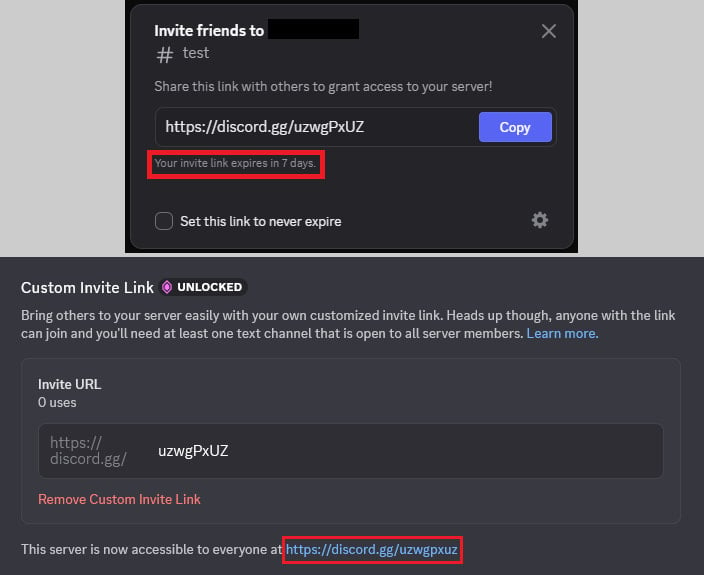
Lowercase character invite codes remain locked to their original server for the duration of their validity, but uppercase codes can be duplicated in vanity links when converted to lowercase, regardless of the original’s status.
Redirection to Malicious Domains
Cybercriminals are actively monitoring expired and deleted Discord invites, leveraging these links in a campaign that has already compromised approximately 1,300 users across the US, UK, France, the Netherlands, and Germany, as reported by Check Point.
These attackers are repurposing legitimate discord invite links from established communities, disseminating them via social media platforms and community websites. To add to the illusion of legitimacy, these malicious servers are designed to appear credible.
The compromised Discord servers restrict users to a single channel, #verify, where a bot initiates a verification process.
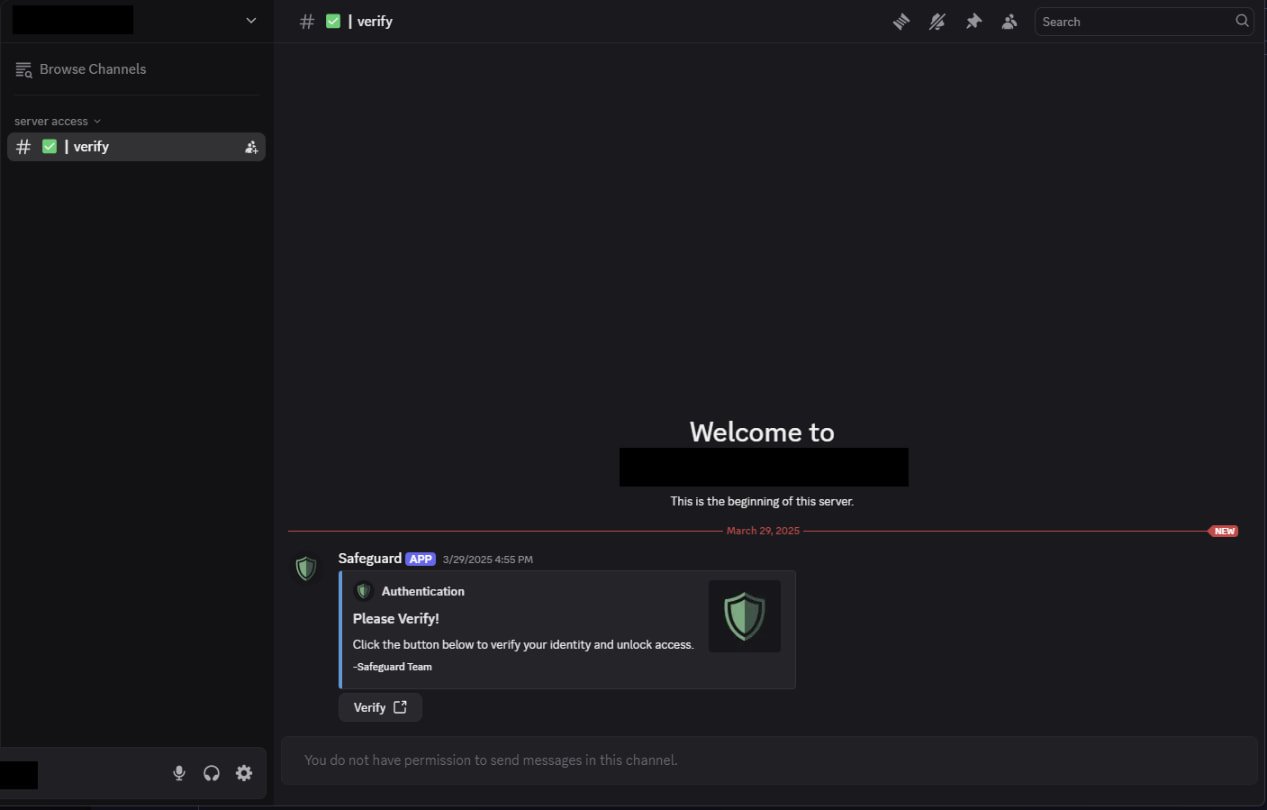
The verification attempts redirect users to a fraudulent website mimicking the Discord interface, falsely claiming a CAPTCHA issue. Users are manipulated into executing a PowerShell command that they are led to copy from the page.
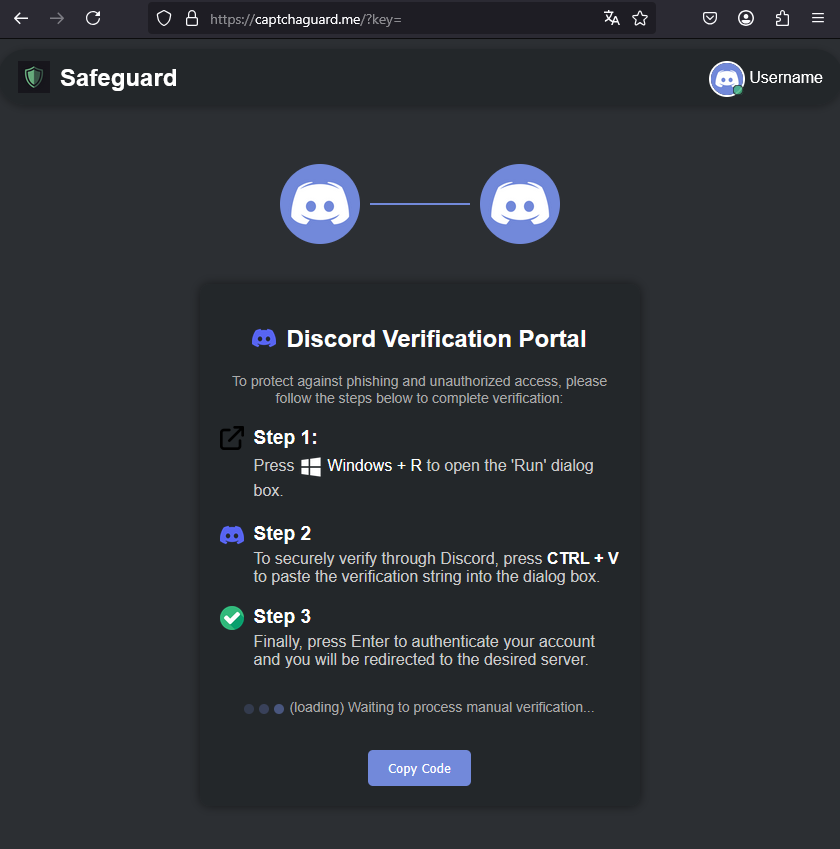
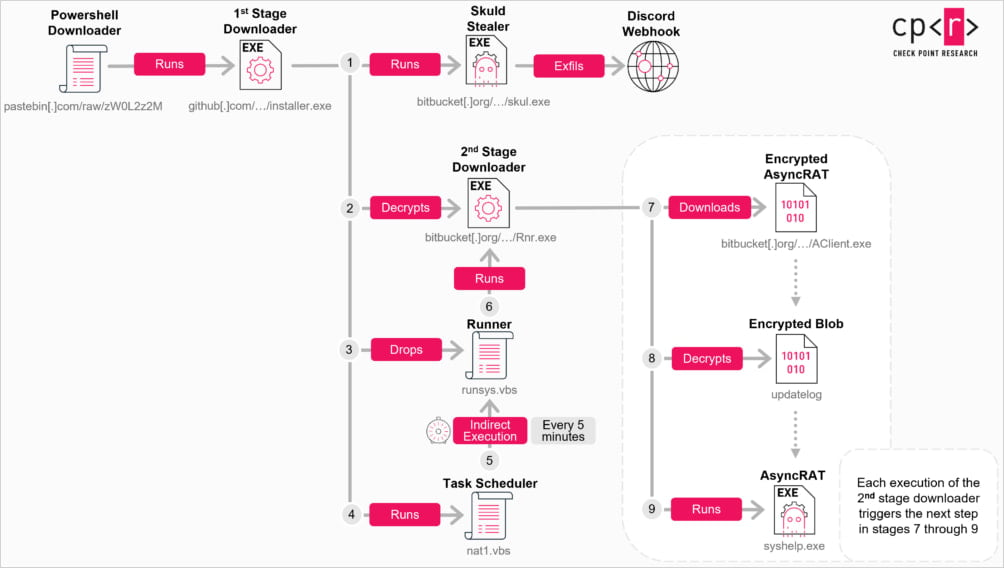
This action triggers a multi-stage infection involving various methodologies, including PowerShell downloaders, obfuscated C++ loaders, and VBScript files.
Subsequently, malicious payloads download from the legitimate Bitbucket platform and may include:
- AsyncRAT: Provided as ‘AClient.exe,’ this malware enables extensive operations such as file retrieval, keylogging, and unauthorized access to microphones and webcams.
- Skuld Stealer: Distributed under ‘skul.exe,’ this info-stealer targets browser credentials, cookies, Discord tokens, and cryptocurrency wallet details, utilizing JavaScript to extract sensitive information via Discord webhooks.
- ChromeKatz: A customized variant of an open-source utility, delivered as ‘cks.exe,’ designed to exfiltrate cookies and passwords.
A scheduled task is established on the infected system to ensure the malware loader restarts at five-minute intervals, as discovered by researchers.
To mitigate these risks, it is imperative for Discord users to exercise caution with old invite links, particularly those originating from outdated posts. Additionally, users should critically assess “verification” requests and refrain from executing PowerShell commands without thorough understanding.
Server administrators are strongly advised to utilize permanent invites, as they are substantially more secure against hijacking attempts.








