Criminal Proxy Network Compromises Thousands of IoT Devices
A criminal proxy network has been identified as infecting thousands of Internet of Things (IoT) and end-of-life (EoL) devices, repurposing them into a substantial botnet that facilitates anonymity for malicious online activities.
This extensive network has been under scrutiny for the past year, tracked by Lumen’s Black Lotus Labs in collaboration with the U.S. Department of Justice, the FBI, and the Dutch National Police. It primarily exploits outdated residential devices, forming a network that serves as anonymizing proxies for cybercriminals.
The infrastructure is mainly situated in Turkey and encompasses five servers, including one that reportedly collects data silently via UDP.
How the Proxy Network Operates
The botnet targets unprotected IoT and Small Office/Home Office (SOHO) devices, many of which lack ongoing security updates. Lumen’s telemetry data indicates an average of 1,000 active proxies per week across over 80 countries, with the highest concentration of affected devices identified in the United States, followed by Ecuador and Canada.
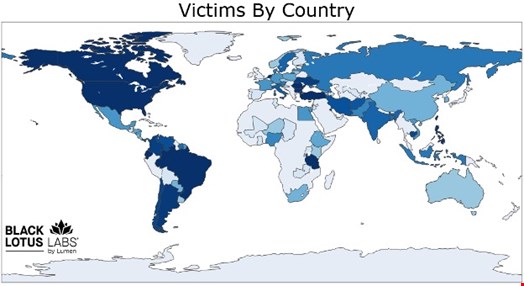
Devices compromised by this malicious software become part of a proxy-for-rent service. Unauthorized users can purchase temporary access to these devices, allowing them to route their traffic anonymously. Notably, this system does not require authentication, offering open access to anyone who identifies the correct IP address and port. Malicious actions facilitated by this proxy network include:
– Ad fraud
– Distributed Denial of Service (DDoS) attacks
– Brute-force credential stuffing
– Data exploitation
The infected devices enable cybercriminals to obscure their activities within legitimate residential traffic. Alarmingly, only about 10% of these proxies are flagged as malicious by tools like VirusTotal.
The operators of the network claim to maintain over 7,000 active proxies daily; however, Lumen estimates that this figure is likely inflated. Regardless, the service’s operational stability and global reach present ongoing hurdles for cybersecurity defenders.
Law Enforcement Disruption Efforts
Lumen, alongside law enforcement agencies, has achieved some success in disrupting the established command-and-control infrastructure of the network by null routing traffic through Lumen’s backbone. Nevertheless, the abundance of vulnerable devices guarantees that threats of this nature will continue to persist.
Researchers noted that “anonymity is the key to success for criminals of all types.” The network’s operators have managed to maintain a low profile to evade detection. They are leveraging equipment that has surpassed the vendor support lifecycle, which renders the devices unpatchable and unprotected.
To mitigate similar threats, security professionals recommend implementing the following measures:
– Monitoring for abnormal login attempts originating from residential IP addresses.
– Blocking known open proxy addresses.
– Replacing end-of-life devices and ensuring that routers are kept up to date with security enhancements.
Black Lotus Labs has pledged to continue sharing intelligence with global partners and emphasizes the importance of proactive monitoring for indicators of compromise related to similar networks.








