Clarification: The 16 Billion Credentials Leak Is Not a Recent Data Breach

Recent reports have emerged regarding a significant breach, touted as the “mother of all breaches,” which quickly garnered extensive media attention filled with alarmist narratives. However, initial assessments reveal that the information in question consists of previously disclosed credentials acquired through infostealers, data breaches, and credential stuffing attacks rather than representing a new or recent breach of security.
It is crucial to clarify that this incident does not signify a new breach; the websites involved were not re-compromised for these credentials. The credentials that have surfaced are believed to have been in circulation for an extensive period, possibly even years, and have been amassed by a cybersecurity entity, researchers, or threat actors—ultimately repackaged into a database that was briefly made available online.
A recent finding by Cybernews indicated that the exposed compilation was formatted in a manner typical of infostealer malware, although they did not provide specific samples for analysis.
Infostealers are a class of malware designed to capture sensitive information such as credentials, cryptocurrency wallets, and other data from infected systems. Over the past few years, they have become a pervasive threat, leading to numerous security incidents globally.
This malware affects both Windows and macOS systems. When executed, it systematically gathers available credentials stored on the victim’s device and compiles them into what is referred to as a “log.”
An infostealer log is essentially an archive filled with various text files and other types of stolen data, detailing lists of credentials harvested from browsers, files, and applications.
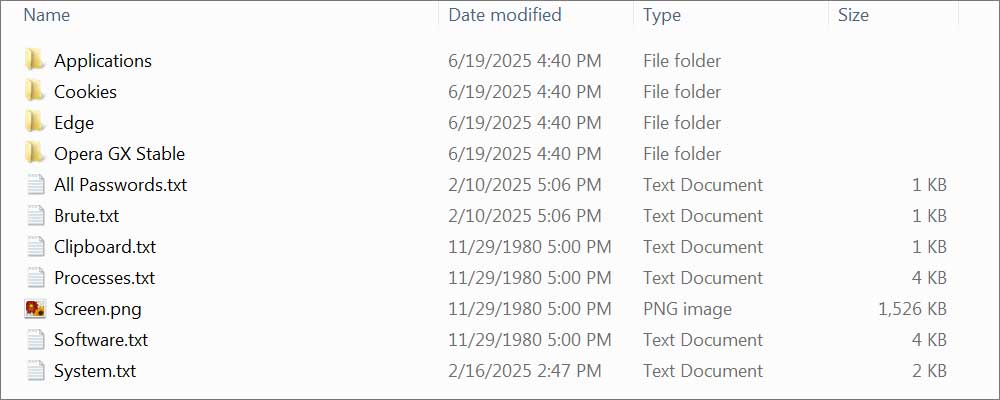
Source: BleepingComputer
The stolen credentials are generally formatted with one entry per line, structured as follows:
URL:username:password
Occasionally, the separating character between components may be altered to a comma, semicolon, or dash.
For example, the credentials obtained by an infostealer may be stored in the log as:
https://www.facebook.com/:[email protected]:Databr3achFUd!
https://www.bank.com/login.php:jsmith:SkyIsFa11ing#
https://x.com/i/flow/login:[email protected]:StayCalmCarryOn
When a device is compromised by an infostealer, it can potentially extract all stored credentials, resulting in significant data loss, which is later uploaded to the threat actor responsible for the malware. These credentials can subsequently be utilized for further cyber-attacks or sold on illicit marketplaces.
The issue of infostealers has escalated to the point where compromised credentials have become one of the most prevalent avenues for cyber adversaries to infiltrate networks.
In response, law enforcement agencies worldwide have intensified efforts to dismantle such cybercrime operations, evident in recent initiatives, including “Operation Secure” and actions targeting the LummaStealer malware operation.
Due to the widespread availability of infostealers and the resulting compilations, threat actors frequently distribute extensive lists of stolen credentials for free via platforms like Telegram, Pastebin, and Discord. This practice not only enhances their standing in the cybercriminal community but also serves as a marketing strategy for their paid offerings.
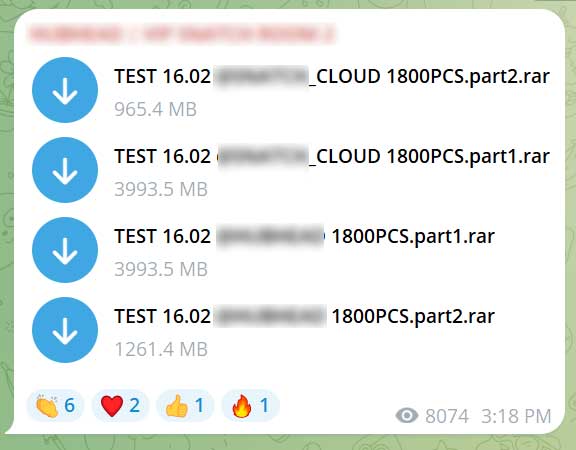
Source: BleepingComputer
One specific instance revealed a file totaling 1,261.4 MB, containing over 64,000 credential pairs made available at no cost.
Countless similar leaked archives are proliferating online, contributing to billions of credential records being liberally released.
The origins of many of these free archives likely correlate with the substantial database recently identified by Cybernews.
Historical instances of similar credential collections include the RockYou2024 leak, comprising over 9 billion records, and the earlier Collection #1, which included more than 22 million distinct passwords.
Despite the prevailing discussion, there is no substantiated evidence to suggest that this compilation contains fresh or unrecorded data.
Recommended Actions
In light of the recent revelation involving a substantial leak of credentials, it is essential to understand the proper steps to take in response.
The foremost action is to adopt and sustain robust cybersecurity practices that should already be implemented.
If you suspect that an infostealer may be operating on your machine, it is imperative to conduct a thorough scan using trusted antivirus software before altering any passwords; otherwise, newly created credentials could be compromised as well.
Once confidence is established in your system’s integrity, prioritize enhancing your password management strategies.
This encompasses utilizing a unique, strong password for each account you access and leveraging a password manager for administration and security purposes.
That said, employing distinct passwords may not sufficiently safeguard you against hacking, phishing attempts, or insidious malware installations.
Consequently, it remains critical to enable two-factor authentication (2FA) in conjunction with an authentication application such as Microsoft Authenticator, Google Authenticator, or Authy for managing your 2FA codes. Certain password managers like Bitwarden and 1Password also incorporate authentication capabilities, consolidating both functionalities within a single application.
By enabling 2FA, even if a password is compromised, unauthorized individuals will be unable to gain access without your 2FA code.
As a prudent measure, refrain from utilizing SMS as a method for receiving 2FA codes, as adversaries can engage in SIM-swapping tactics to gain access to your phone number and intercept these codes.
Concerning this leak, it is plausible that some readers may find their information present in the compilation.
However, it is advisable to remain calm and not hastily change all your passwords. Instead, utilize this moment to bolster your cybersecurity habits.
To assess whether your credentials have been involved in prior breaches, consider utilizing services such as Have I Been Pwned.
If you have previously utilized the same password across multiple platforms, now is the ideal time to transition to unique credentials.
This approach significantly mitigates the potential impact of such leaks on your security posture.








