Exploitation of SAP Vulnerability by Ransomware Syndicates and State-Sponsored Threat Actors
Cybersecurity researchers have identified that a critical vulnerability in SAP’s NetWeaver Visual Composer development server is being actively exploited by various threat actors. This includes ransomware groups such as BianLian and RansomwEXX, as well as a nation-state threat actor linked to China, referred to as Chaya_004.
Strong Evidence of Exploitation
The flaw, designated CVE-2025-31324, is classified as an unauthenticated file upload vulnerability found in the Metadata Uploader component of SAP NetWeaver Visual Composer Framework version 7.50. SAP has assigned this vulnerability the highest severity score of 10.0 (CVSS v3.1). It allows unauthenticated attackers to upload potentially harmful executable binaries, posing a significant risk to the host system.
The vulnerability was first discovered by ReliaQuest on April 22, with SAP publicly disclosing it two days later in a security advisory that included a patch, which is only accessible to SAP customers. Early evidence of exploitation emerged swiftly; notably, the Shadowserver Foundation reported over 400 NetWeaver servers exposed to the internet.
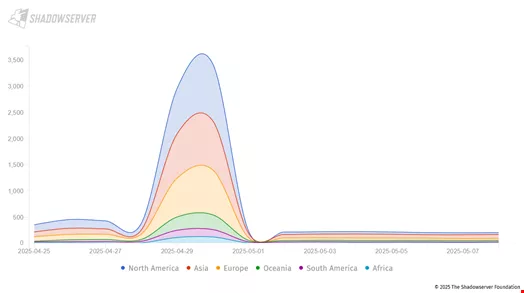
Further investigations by private security firms, including Onapsis and WatchTowr, have confirmed the exploitation of CVE-2025-31324, with attackers utilizing web shell backdoors on unpatched instances accessible online. On April 27, Onapsis, in collaboration with Google Cloud-owned Mandiant, released an open-source tool for identifying potential compromises in affected SAP systems. Subsequently, on April 29, the US Cybersecurity and Infrastructure Security Agency (CISA) added CVE-2025-31324 to its Known Exploited Vulnerabilities (KEV) catalog.
In addition, on May 13, SAP disclosed another critical flaw, CVE-2025-42999, which is associated with CVE-2025-31324 and also affects SAP NetWeaver Visual Composer.
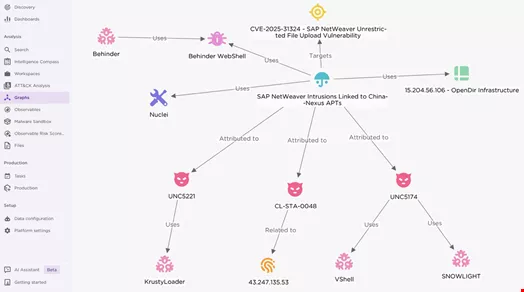
Chinese Nation-State Exploiting CVE-2025-31324
Forescout’s Federe Labs released a report on May 8, revealing that a Chinese nation-state actor was likely using CVE-2025-31324 for malicious campaigns. It noted the establishment of potentially malicious infrastructure which included servers hosting Supershell backdoors, often deployed on Chinese cloud providers, alongside various penetration testing tools of Chinese origin.
The attacks identified involved IP addresses that employed anomalous self-signed certificates impersonating legitimate services like Cloudflare. Many of the IP addresses traced back to Chinese cloud service providers, such as Alibaba and Tencent.
Another analysis by EclectiIQ indicated with high confidence that certain intrusions into SAP NetWeaver environments were linked to Chinese cyber-espionage units, reflecting strong connections to the Ministry of State Security or affiliated entities.
Ransomware Groups Exploiting CVE-2025-31324
Alongside state actors, ReliaQuest reported on May 14 that ransomware groups have also been exploiting CVE-2025-31324. The company noted with moderate confidence that BianLian was involved in incidents of exploitation. They identified a server hosting services initiated by malicious executables, indicating links to previously flagged command-and-control infrastructure associated with the ransomware group.
Additionally, separate incidents were reported where attackers leveraged the SAP vulnerability to deploy ‘PipeMagic,’ a modular backdoor connected to RansomEXX. This was delivered through MSBuild abuse, showcasing a broader trend among threat actors to weaponize prominent vulnerabilities for financial exploitation.
These developments underscore the critical urgency for organizations to apply patches immediately, enhance monitoring for suspicious activities, and bolster defensive measures against these escalating threats.








