Vulnerabilities in Bluetooth Technology May Enable Unauthorized Audio Surveillance
Vulnerabilities in a widely used Bluetooth chipset have been identified, posing risks of eavesdropping and data theft. This chipset, found in over 29 audio devices from notable manufacturers such as Beyerdynamic, Bose, Sony, Marshall, Jabra, JBL, Jlab, EarisMax, MoerLabs, and Teufel, can potentially be exploited by attackers.
The affected devices include various speakers, earbuds, headphones, and wireless microphones. Attackers can compromise these devices to gain access to sensitive information, including call history and contacts on connected mobile devices.
At the recent TROOPERS security conference in Germany, cybersecurity experts from ERNW disclosed three significant vulnerabilities associated with Airoha systems on a chip (SoCs), commonly used in True Wireless Stereo (TWS) earbud technology. Although the vulnerabilities are not rated as critical, they do necessitate close physical proximity and a level of technical expertise for exploitation. The identified vulnerabilities include:
- CVE-2025-20700: Missing authentication for GATT services (medium severity).
- CVE-2025-20701: Missing authentication for Bluetooth BR/EDR (medium severity).
- CVE-2025-20702: Critical capabilities of a custom protocol (high severity).
Researchers successfully crafted a proof-of-concept exploit that enabled them to extract currently playing media information from affected headphones.
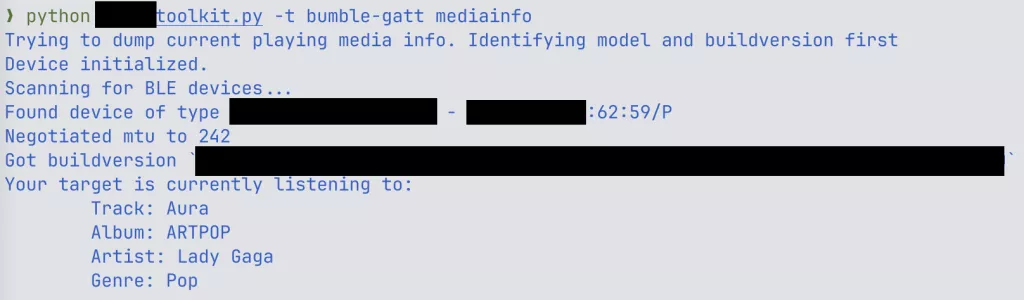
While the initial findings represent a moderate threat, further exploitation could allow attackers to hijack Bluetooth connections, interfacing directly with mobile devices and utilizing the Bluetooth Hands-Free Profile (HFP) to execute commands. They could also initiate calls or access sensitive data, such as a user’s call history.
Additionally, exploitation of these vulnerabilities could enable remote code execution by rewriting the firmware of affected devices, facilitating the spread of potentially wormable exploits.
Despite the serious nature of these vulnerabilities, their real-world application remains limited. Effective exploitation would require not only technical expertise but also physical proximity, restricting the feasibility to high-value targets like governmental officials, journalists, and others in critical fields.
In response to the identified vulnerabilities, Airoha has implemented an updated software development kit (SDK) to address these security issues, while manufacturers are in the process of developing and distributing necessary patches. However, reports indicate that more than half of the affected devices have firmware updates released prior to the availability of the new SDK, highlighting the urgency for users to remain vigilant regarding potential security risks.








