CoinMarketCap Experiences Security Breach Resulting in Cryptocurrency Wallet Exploitation through Deceptive Web3 Pop-up
CoinMarketCap, a leading cryptocurrency price tracking platform, experienced a significant security breach that resulted in the unauthorized draining of crypto wallets from unsuspecting visitors. On January 20, 2025, users encountered deceptive Web3 popups prompting them to connect their wallets. Upon doing so, a malicious script was executed, leading to the theft of funds.
The incident stemmed from a vulnerability associated with an image on the site’s homepage, referred to as a “doodle.” This vulnerability enabled threat actors to inject harmful JavaScript into the site. In a statement, CoinMarketCap’s security team affirmed their immediate response to remove the compromised content and implement measures to prevent future incidents. They assured users that all systems were restored and secured.
Cybersecurity experts from c/side detailed the mechanics of the attack, highlighting how attackers modified the application programming interface (API) that CoinMarketCap utilized to fetch the doodle image. The tampered JSON payload introduced a malicious script tag that led to a wallet drainer exploit. This fake wallet connection prompt closely mimicked genuine Web3 transaction requests, ultimately targeting users’ assets.
c/side characterized this as a supply chain attack, signifying that the breach occurred not through CoinMarketCap’s own servers but via a third-party resource. Such attacks are notoriously challenging to detect, as they manipulate components that users typically trust.
Further insights emerged from a threat actor, Rey, who claimed that the attackers shared a screenshot of their illicit operations on a Telegram channel. This information revealed that approximately $43,266 had been stolen from around 110 victims, with discussions conducted in French within the group.
The incidence underscores the growing threat posed by wallet drainers, which have surged in prevalence alongside the rise of the cryptocurrency market. Unlike traditional phishing schemes, wallet draining tactics are often propagated through social media, advertisements, spoofed websites, and malicious browser extensions.
Recent reports indicate that these sophisticated attacks led to nearly $500 million being stolen in 2024, impacting over 300,000 wallet addresses. In response to this growing problem, Mozilla has introduced a new detection system aimed at identifying wallet drainers within the Firefox Add-on repository, reflecting the urgent need for enhanced security measures in the crypto space.
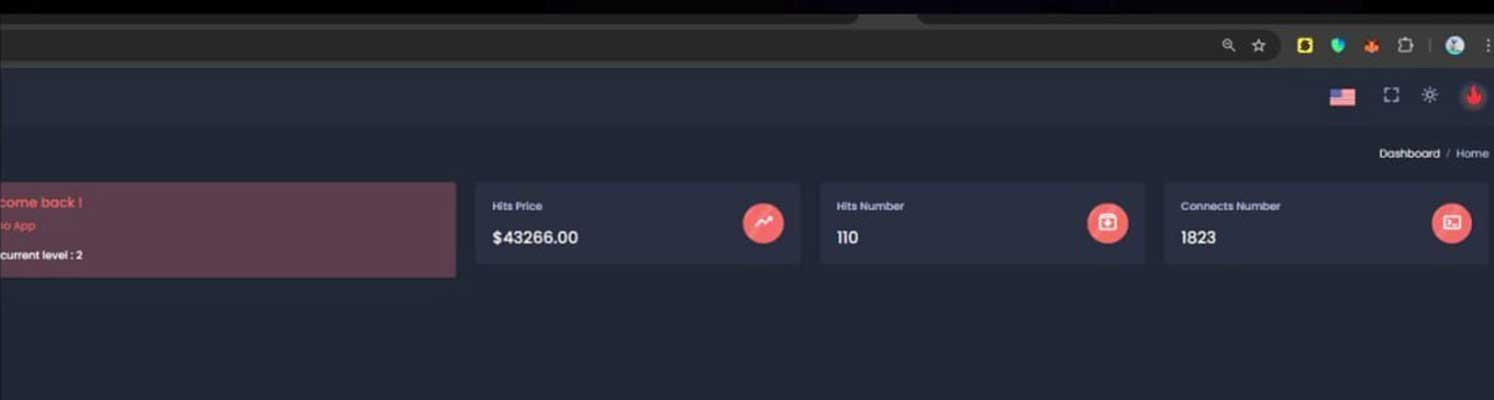
Screenshot of drainer panel shared on Telegram
Source: Rey








