U.S. Authorities Indict Additional 12 Individuals in Connection with $230 Million Cryptocurrency Theft

In a significant law enforcement action, twelve additional individuals have been charged as part of a RICO conspiracy connected to a cyber theft exceeding $230 million in cryptocurrency. The suspects allegedly engaged in various fraudulent activities to misappropriate digital assets and subsequently launder the proceeds through multiple cryptocurrency exchanges and mixing services.
This follows the earlier apprehension of two suspects, Malone Lam (age 20), known by aliases including “Greavys,” “Anne Hathaway,” and “$$$,” and Jeandiel Serrano (age 21), who is referenced as “Box,” “VersaceGod,” and “@SkidStar.” They were charged in September 2024 for their roles in this extensive scheme.
Court documents reveal that Lam, Serrano, and their co-conspirators exploited victims’ cryptocurrency accounts by obtaining unauthorized access and shifting funds to wallets under their control. Notably, an incident on August 18 resulted in the theft of over 4,100 Bitcoin from a victim in Washington, D.C., valued at over $230 million at the time of the incident.
According to crypto fraud investigator ZachXBT, who assisted with the FBI investigation, the perpetrators specifically targeted a creditor of the Genesis cryptocurrency exchange, utilizing spoofed phone numbers and impersonating customer support representatives from Google and Gemini. During the deception, they successfully convinced the victim to reset two-factor authentication (2FA) and share their screen via AnyDesk, allowing the hackers to access private keys and ultimately siphon off the victim’s cryptocurrency assets.
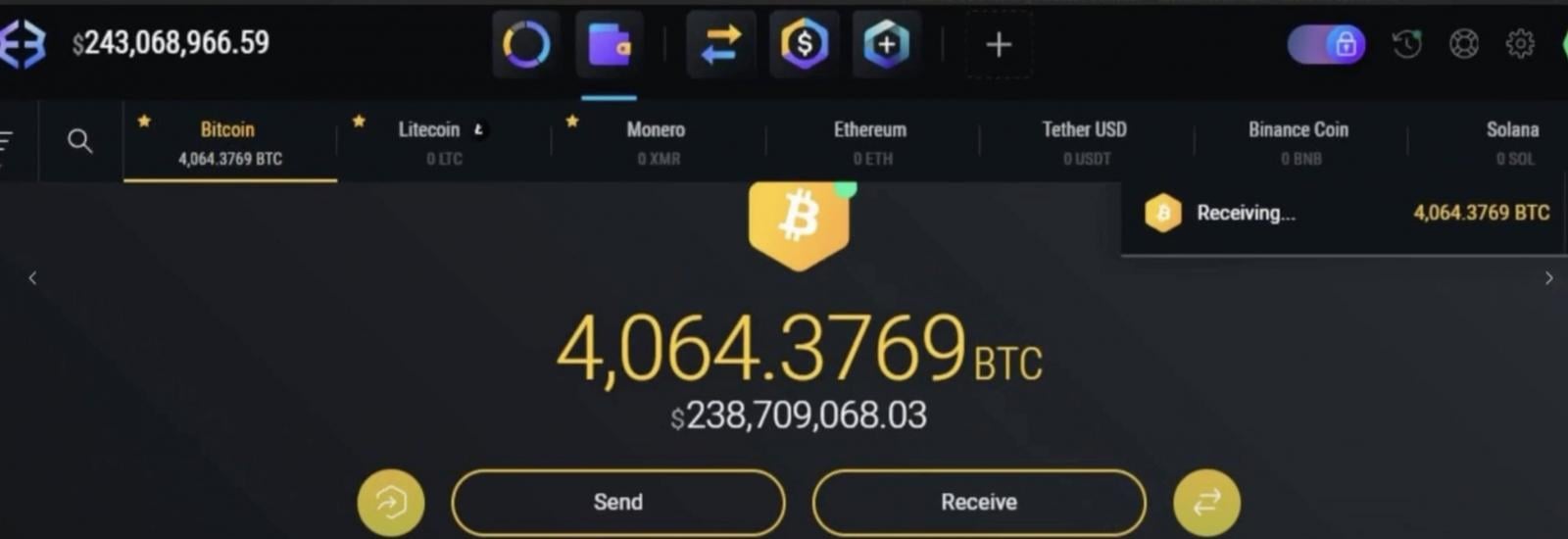
“Initial tracing indicated $243 million was distributed among various individuals before the funds were rapidly transferred to over 15 exchanges, transitioning between Bitcoin, Litecoin, Ethereum, and Monero,” stated ZachXBT.
In addition to cyber racketeering and money laundering charges, the newly indicted defendants are also accused of obstruction of justice and conspiracy to commit wire fraud. The latest defendants include:
- Marlon Ferro, 19 (Santa Ana, California)
- Hamza Doost, 21 (Hayward, California)
- Conor Flansburg, 21 (Newport Beach, California)
- Kunal Mehta, 45 (Irvine, California)
- Ethan Yarally, 18 (Richmond Hill, New York)
- Cody Demirtas, 19 (Stuart, Florida)
- Aakash Anand, 22 (New Zealand)
- Evan Tangeman, 21 (Newport Beach, California)
- Joel Cortes, 21 (Laguna Niguel, California)
- Unknown Defendant 1 aka “Chen” and “Squiggly” (location unknown)
- Unknown Defendant 2 aka “Danny” and “Meech” (location unknown)
- John Tucker Desmond, 19 (Huntington Beach, California)
Despite efforts to obscure their activities through conversion to Monero and other anonymizing techniques, the attackers made critical mistakes that inadvertently linked the laundered funds to the stolen cryptocurrencies.
The laundering operations allegedly employed a variety of sophisticated methods including crypto mixers, exchanges, pass-through wallets, “peel chains,” and virtual private networks (VPNs) to obfuscate their identities and operational locations.
The illicitly obtained cryptocurrency was purportedly utilized to sustain extravagant lifestyles, with reports indicating expenditures on luxury vehicles, high-end watches, designer handbags, nightclub outings, and extensive international travel. U.S. Department of Justice prosecutors illuminated the scale of these transactions, detailing expenses associated with nightclub services that could reach $500,000 per evening, and luxury items valued in the tens of thousands, including lavish homes in Los Angeles, the Hamptons, and Miami, alongside private jet rentals and a fleet of exotic cars valued at up to $3.8 million.
Members of the criminal enterprise assumed varying roles encompassing database hackers, organizers, target identifiers, callers, and money launderers, collaboratively orchestrating a sophisticated network for executing these cyber offenses.








